Security News

In 2021, over 59 million Americans said they lost money as a result of phone scams, with an average reported loss of $502. "Fraud is a major consideration in the telecom industry," said Dr. Gadi Solotorevsky, CTO at Amdocs cVidya, an AI solutions provider. In past practice, the telecom industry handled fraud complaints manually.

A state-sponsored threat actor allegedly affiliated with Iran has been linked to a series of targeted attacks aimed at internet service providers and telecommunication operators in Israel, Morocco, Tunisia, and Saudi Arabia, as well as a ministry of foreign affairs in Africa, new findings reveal. The intrusions, staged by a group tracked as Lyceum, are believed to have occurred between July and October 2021, researchers from Accenture Cyber Threat Intelligence group and Prevailion's Adversarial Counterintelligence Team said in a technical report.

China's Ministry of Industry and Information Technology has responded with mild indignation to the USA's decision to revoke the operating licence that allowed China Telcom to operate in the land of the free. In a Wednesday statement, the Ministry accused the USA of using national security as a pretext for banning Chinese companies, complained that evidence of China Telecom's alleged misdeeds has not been furnished, and that the ban breaches international trade rules.

China Telecom Americas is the largest foreign subsidiary of China Telecom Corporation, China's state-owned telecom company. "Indeed, the FCC's own review found that China Telecom Americas poses significant national security concerns due to its control and ownership by the Chinese government, including its susceptibility to complying with communist China's intelligence and cybersecurity laws that are contrary to the interests of the United States."

The US Federal Communications Commission has terminated China Telecom's authority to provide communications services in the USA. In its announcement of the termination, the government agency explained the decision is necessary because the national security environment has changed in the years since 2002. That was when China Telecom was first allowed to operate in the USA. The FCC now believes - partly based on classified advice from national security agencies - that China Telecom can "Access, store, disrupt, and/or misroute U.S. communications, which in turn allow them to engage in espionage and other harmful activities against the United States".

A highly sophisticated adversary named LightBasin has been identified as behind a string of attacks targeting the telecom sector with the goal of collecting "Highly specific information" from mobile communication infrastructure, such as subscriber information and call metadata. Known to be active as far back as 2016, LightBasin is believed to have compromised 13 telecommunication companies across the world since 2019 by leveraging custom tools and their extensive knowledge of telecommunications protocols for scything through organizations' defenses.

A group of hackers that security researchers call LightBasin has been compromising mobile telecommunication systems across the world for the past five years. LightBasin is active since at least 2016 and targets Linux and Solaris servers in particular, although it did interact with Windows systems where needed, in their mission to steal subscriber information and call metadata.
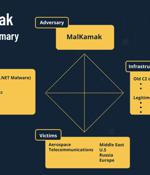
Details have emerged about a new cyber espionage campaign directed against the aerospace and telecommunications industries, primarily in the Middle East, with the goal of stealing sensitive information about critical assets, organizations' infrastructure, and technology while remaining in the dark and successfully evading security solutions. "The ShellClient RAT has been under ongoing development since at least 2018, with several iterations that introduced new functionalities, while it evaded antivirus tools and managed to remain undetected and publicly unknown," researchers Tom Fakterman, Daniel Frank, Chen Erlich, and Assaf Dahan said in a technical deep dive published today.

Published by Cybereason, the report said that it found evidence of three different clusters of attacks going back to at least 2017, all perpetrated by groups or individuals connected in some way to advanced persistent threat groups Soft Cell, Naikon and Group-3390, which have each operated for the Chinese government in the past. Cybereason said it believes the goal of the attacks was to established continuous access to telecom provider records "And to facilitate cyber espionage by collecting sensitive information, compromising high-profile business assets such as the billing servers that contain Call Detail Record data, as well as key network components such as the Domain Controllers, Web Servers and Microsoft Exchange servers."

Britain's Telecoms Security Bill will be accompanied by a detailed code of practice containing 70 specific security requirements for telcos and their suppliers to meet, The Register can reveal. The Telecom Security Bill, which is near the end of its journey through Parliament, has been rather unpopular with some ISPs who have previously complained about the high cost of compliance.