Security News

Remember Bucket Monopoly? Yeah, it gets worse Amazon Web Services has fixed a flaw in its open source Cloud Development Kit that, under the right conditions, could allow an attacker to hijack a...
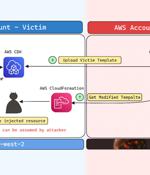
Cybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted in an account takeover under specific...

A critical vulnerability in NVIDIA Container Toolkit impacts all AI applications in a cloud or on-premise environment that rely on it to access GPU resources. [...]

33% of cloud environments using the toolkit impacted, we're told A critical bug in Nvidia's widely used Container Toolkit could allow a rogue user or software to escape their containers and...

Cybersecurity researchers have discovered a new version of an Android banking trojan called Octo that comes with improved capabilities to conduct device takeover (DTO) and perform fraudulent...

Yet, another critical severity vulnerability has been discovered in LiteSpeed Cache, a caching plugin for speeding up user browsing in over 6 million WordPress sites. [...]

Account takeover attacks have emerged as one of the most persistent and damaging threats to cloud-based SaaS environments. Yet despite significant investments in traditional security measures,...

A critical vulnerability in the LiteSpeed Cache WordPress plugin can let attackers take over millions of websites after creating rogue admin accounts. [...]
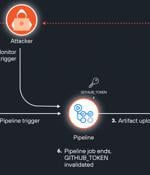
A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations' cloud environments."A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them available for anyone with read access to the repository to consume," Palo Alto Networks Unit 42 researcher Yaron Avital said in a report published this week.
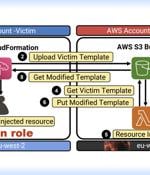
Central to the issue, dubbed Bucket Monopoly, is an attack vector referred to as Shadow Resource, which, in this case, refers to the automatic creation of an AWS S3 bucket when using services like CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar. An attacker could take advantage of this behavior to set up buckets in unused AWS regions and wait for a legitimate AWS customer to use one of the susceptible services to gain covert access to the contents of the S3 bucket.