Security News


Cybersecurity researchers have uncovered new stealer malware that's designed to specifically target Apple macOS systems. Dubbed Banshee Stealer, it's offered for sale in the cybercrime underground...

Microsoft warned customers this Tuesday to patch a critical TCP/IP remote code execution (RCE) vulnerability with an increased likelihood of exploitation that impacts all Windows systems with IPv6...

Microsoft warned customers this Tuesday to patch a critical TCP/IP remote code execution (RCE) vulnerability with an increased likelihood of exploitation that impacts all Windows systems with IPv6...

Hackers targeted AutoCanada in a cyberattack last Sunday that impacted the automobile dealership group's internal IT systems, which may lead to disruptions. [...]

Cybersecurity researchers have identified a number of security shortcomings in photovoltaic system management platforms operated by Chinese companies Solarman and Deye that could enable malicious actors to cause disruption and power blackouts. "If exploited, these vulnerabilities could allow an attacker to control inverter settings that could take parts of the grid down, potentially causing blackouts," Bitdefender researchers said in an analysis published last week.
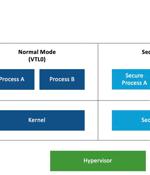
Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the Windows files with older versions. The second vulnerability also concerns a case of privilege escalation in Windows systems that support VBS, effectively allowing an adversary to replace current versions of Windows system files with outdated versions.

SafeBreach security researcher Alon Leviev discovered a Windows Update downgrade attack that can "unpatch" fully-updated Windows 10, Windows 11, and Windows Server systems to reintroduce old...

US law enforcement and cybersecurity agencies are reminding the public that the country's voting systems will remain unaffected by distributed denial of service attacks as the next presidential election fast approaches. The feds didn't go as far as to say they expected DDoS attacks to strike the November election, but they did comment on how popular a tactic they are among politically and ideologically motivated hacktivists and cybercriminals.

French judicial authorities, in collaboration with Europol, have launched a so-called "Disinfection operation" to rid compromised hosts of a known malware called PlugX. The Paris Prosecutor's Office, Parquet de Paris, said the initiative was launched on July 18 and that it's expected to continue for "Several months." The development comes nearly three months after French cybersecurity firm Sekoia disclosed it sinkhole a command-and-control server linked to the PlugX trojan in September 2023 by spending $7 to acquire the IP address.