Security News

Threat actors have been leveraging zero and n-day vulnerabilities in Cisco security appliances (CVE-2024-20481), Microsoft Sharepoint (CVE-2024-38094), and Google’s Chrome browser (CVE-2024-4947)....

Plus, a POC to make it extra easy for attackers A Microsoft SharePoint bug that can allow an attacker to remotely inject code into vulnerable versions is under active exploitation, according to...
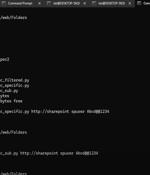
A high-severity flaw impacting Microsoft SharePoint has been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on...

Varonis Threat Labs researchers have uncovered two techniques attackers can use can use for covert data and file exfiltration from companies' SharePoint server. "These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync events," they noted.

Researchers have discovered two techniques that could enable attackers to bypass audit logs or generate less severe entries when downloading files from SharePoint. Microsoft SharePoint is a web-based collaborative platform that integrates with Microsoft Office and 365, primarily as a document management and data storage system.

The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2023-24955 – a code injection vulnerability that allows authenticated attackers to execute code remotely on a vulnerable...

CISA warns that attackers are now exploiting a Microsoft SharePoint code injection vulnerability that can be chained with a critical privilege escalation flaw for pre-auth remote code execution attacks. These two SharePoint Server security vulnerabilities can be chained by unauthenticated attackers to gain RCE on unpatched servers, as STAR Labs researcher Nguyễn Tiến Giang demonstrated during last year's March 2023 Pwn2Own contest in Vancouver.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting the Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on...

Security experts claim ransomware criminals have got their hands on a functional exploit for a nearly year-old critical Microsoft SharePoint vulnerability that was this week added to the US's must-patch list. Without specifically identifying the gang, researcher Kevin Beaumont said that at least one ransomware group has a working exploit for the critical vulnerability, which can potentially achieve remote code execution although the US Cybersecurity and Infrastructure Security Agency said its use in ransomware campaigns is currently "Unknown."

CISA warns that attackers are now exploiting a critical Microsoft SharePoint privilege escalation vulnerability that can be chained with another critical bug for remote code execution. This Microsoft SharePoint Server exploit chain was successfully demoed by STAR Labs researcher Jang during last year's March 2023 Pwn2Own contest in Vancouver, earning a $100,000 reward.