Security News
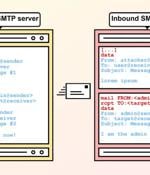
A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized by threat actors to send spoofed emails with fake sender addresses while bypassing security...

Steam is no longer supported on Windows 7, Windows 8, and Windows 8.1 as of January 1, with the company recommending users upgrade to a newer operating system. "As of January 1 2024, Steam will officially stop supporting the Windows 7, Windows 8 and Windows 8.1 operating systems," reads the support article.

Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell (SSH) cryptographic network protocol that could allow an attacker to downgrade the connection's...

Japanese game developer Ateam has proven that a simple Google Drive configuration mistake can result in the potential but unlikely exposure of sensitive information for nearly one million people over a period of six years and eight months. Setting Google Drive to "Anyone with the link can view" makes it viewable only to those with the exact URL, typically reserved for collaboration between people working with non-sensitive data.

Organizations with mainframes face a unique challenge: extending consistency across the entire enterprise, including mainframe environments. A common discrepancy arises as the IAM system used in the enterprise often differs from the one employed for mainframe authentication.

In 2024, we anticipate several key trends and predictions that will shape the landscape of API security. The API security market is currently in its early days, but as API security climbs the business agenda, we expect to see significant innovation in this space.

The immense amount of time IT leaders are spending on IT support is even more shocking given that 46% of respondents say that they are already in an advanced state of AI adoption with AI already prevalent throughout their organization. While security is a priority for IT leaders at large, just how important it is differs significantly across IT leadership.

When Stolen Device Protection is turned on, Face ID or Touch ID authentication is required for additional actions, including viewing passwords or passkeys stored in iCloud Keychain, applying for a new Apple Card, turning off Lost Mode, erasing all content and settings, using payment methods saved in Safari, and more. No passcode fallback is available in the event that the user is unable to complete Face ID or Touch ID authentication.

These solutions were designed to fight a specific kind of threat and are implemented on an island - not talking to the other security solutions. The relatively new approach called XDR was designed to pull together information from disparate threat detection software like cloud, network and email, to respond to more complex threats by sorting through raw data and alerts and mitigating threats across vectors.

91% of banks and insurance companies have now initiated their cloud journey, a significant increase from 2020, when only 37% of firms had embarked on their cloud transformations, according to Capgemini. "For today's financial services organization, ignoring the cloud is simply not an option. Moving to the cloud requires looking beyond a cost-savings approach and being centered around driving innovation to gain a competitive edge," said Ravi Khokhar, Global Head of Cloud for Financial Services at Capgemini.