Security News
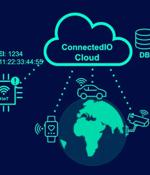
Multiple high-severity security vulnerabilities have been disclosed in ConnectedIO's ER2000 edge routers and the cloud-based management platform that could be exploited by malicious actors to...

Cybersecurity agencies from Japan and the U.S. have warned of attacks mounted by a state-backed hacking group from China to stealthily tamper with branch routers and use them as jumping-off points...

US and Japanese law enforcement and cybersecurity agencies warn of the Chinese 'BlackTech' hackers breaching network devices to install custom backdoors for access to corporate networks. The FBI notice warns that the BlackTech hackers use custom, regularly updated malware to backdoor network devices, which are used for persistence, initial access to networks, and to steal data by redirecting traffic to attacker-controlled servers.

Three critical-severity remote code execution vulnerabilities impact ASUS RT-AX55, RT-AX56U V2, and RT-AC86U routers, potentially allowing threat actors to hijack devices if security updates are not installed.The flaws, which all have a CVSS v3.1 score of 9.8 out of 10.0, are format string vulnerabilities that can be exploited remotely and without authentication, potentially allowing remote code execution, service interruptions, and performing arbitrary operations on the device.

Fortinet has issued an alert warning that the Gafgyt botnet malware is actively trying to exploit a vulnerability in the end-of-life Zyxel P660HN-T1A router in thousands of daily attacks. [...]

More details have emerged about a botnet called AVRecon, which has been observed making use of compromised small office/home office routers as part of a multi-year campaign active since at least May 2021. AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware capable of executing additional commands and stealing victim's bandwidth for what appears to be an illegal proxy service made available for other actors.

Key factors for effective security automationIn this Help Net Security interview, Oliver Rochford, Chief Futurist at Tenzir, discusses how automation can be strategically integrated with human expertise, the challenges in ensuring data integrity, and the considerations when automating advanced tasks. MikroTik vulnerability could be used to hijack 900,000 routersA privilege escalation vulnerability could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines.

A privilege escalation vulnerability (CVE-2023-30799) could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines. While exploting it does require...
A new malware strain has been found covertly targeting small office/home office routers for more than two years, infiltrating over 70,000 devices and creating a botnet with 40,000 nodes spanning 20 countries. Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the third such strain to focus on SOHO routers after ZuoRAT and HiatusRAT over the past year.

Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service. According to Lumen's Black Lotus Labs threat research team, while the AVrecon remote access trojan compromised over 70,000 devices, only 40,000 were added to the botnet after gaining persistence.