Security News

QNAP has fixed a second zero-day vulnerability exploited at the Pwn2Own Ireland 2024 hacking contest to gain a root shell and take over a TS-464 NAS device. [...]

If the first patches don't work, try, try again VMware has pushed a second patch for a critical, heap-overflow bug in the vCenter Server that could allow a remote attacker to fully compromise...

A critical security flaw has been disclosed in the Kubernetes Image Builder that, if successfully exploited, could be abused to gain root access under certain circumstances. The vulnerability,...

It's called leaving the door wide open – especially in Proxmox A critical bug in Kubernetes Image Builder could allow unauthorized SSH access to virtual machines (VMs) thanks to default...

A critical vulnerability in Kubernetes could allow unauthorized SSH access to a virtual machine running an image created with the Kubernetes Image Builder project. [...]

Bug reports made in China Broadcom has emitted a pair of patches for vulnerabilities in VMware vCenter Server that a miscreant with network access to the software could exploit to completely...

Cisco has fixed a command injection vulnerability in the Identity Services Engine (ISE) with public exploit code that lets attackers escalate privileges to root on vulnerable systems. [...]
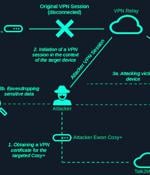
Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks. The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in configuration files, and even get correctly signed X.509 VPN certificates for foreign devices to take over their VPN sessions.

Cybersecurity company CrowdStrike has published its root cause analysis detailing the Falcon Sensor software update crash that crippled millions of Windows devices globally. Specifically, it's related to a problematic content update deployed over the cloud, describing it as a "Confluence" of several problems that led to a crash: A mismatch between the 21 inputs passed to the Content Validator via the IPC Template Type as opposed to the 20 supplied to the Content Interpreter.

Cisco has fixed a critical severity vulnerability that lets attackers add new users with root privileges and permanently crash Security Email Gateway appliances using emails with malicious attachments. "This vulnerability is due to improper handling of email attachments when file analysis and content filters are enabled. A successful exploit could allow the attacker to replace any file on the underlying file system," Cisco explained.