Security News

Security researchers have found a vulnerability in a key air transport security system that allowed unauthorized individuals to potentially bypass airport security screenings and gain access to...

The City of Columbus, Ohio, has filed a lawsuit against security researcher David Leroy Ross, aka Connor Goodwolf, accusing him of illegally downloading and disseminating data stolen from the...

Infosec hounds say they spotted vulnerability during routine travel in the US Cybersecurity researchers say they've found a vulnerability that allowed them to skip US airport security checks and...
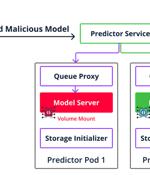
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of more than 20 vulnerabilities that could be exploited to...

Cybersecurity researchers have disclosed a security flaw impacting Microsoft Azure Kubernetes Services that, if successfully exploited, could allow an attacker to escalate their privileges and...

Cybersecurity researchers have discovered new infrastructure linked to a financially motivated threat actor known as FIN7. The two clusters of potential FIN7 activity "indicate communications...

Cybersecurity researchers have discovered two security flaws in Microsoft's Azure Health Bot Service that, if exploited, could permit a malicious actor to achieve lateral movement within customer environments and access sensitive patient data. The critical issues, now patched by Microsoft, could have allowed access to cross-tenant resources within the service, Tenable said in a new report shared with The Hacker News.

Cybersecurity researchers have identified a number of security shortcomings in photovoltaic system management platforms operated by Chinese companies Solarman and Deye that could enable malicious actors to cause disruption and power blackouts. "If exploited, these vulnerabilities could allow an attacker to control inverter settings that could take parts of the grid down, potentially causing blackouts," Bitdefender researchers said in an analysis published last week.
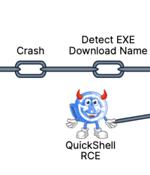
As many as 10 security flaws have been uncovered in Google's Quick Share data transfer utility for Android and Windows that could be assembled to trigger remote code execution chain on systems that have the software installed. "The Quick Share application implements its own specific application-layer communication protocol to support file transfers between nearby, compatible devices," SafeBreach Labs researchers Or Yair and Shmuel Cohen said in a technical report shared with The Hacker News.

Cybersecurity researchers have shed light on a novel Linux kernel exploitation technique dubbed SLUBStick that could be exploited to elevate a limited heap vulnerability to an arbitrary memory...