Security News

The sprawling SolarWinds cyberattack which came to light last December was known for its sophistication in the breadth of tactics used to infiltrate and persist in the target infrastructure, so much so that Microsoft went on to call the threat actor behind the campaign "Skillful and methodic operators who follow operations security best practices to minimize traces, stay under the radar, and avoid detection." By analyzing telemetry data associated with previously published indicators of compromise, RiskIQ said it identified an additional set of 18 servers with high confidence that likely communicated with the targeted, secondary Cobalt Strike payloads delivered via the TEARDROP and RAINDROP malware, representing a 56% jump in the attacker's known command-and-control footprint.

In these new roles, we are struggling to find the top tier of the ever-expanding next generation of threat experts. In career advice calls and meetings with young adults over the past couple of years, I've noticed an unexpected and common pattern emerge with Ivy League fresh grads with cybersecurity degrees, people considering a career transfer with little formal infosec training, and everyone in between.

Grid.ai announced the general availability of Grid, a new platform that enables researchers and data scientists to train AI models on the cloud at scale, from a laptop with zero code changes. The availability of Grid enables AI researchers, machine learning engineers, and data scientists to do development and training at scale without requiring advanced skills in machine learning engineering or MLOps engineering.

An academic researcher has analysed more than 100 Computer Misuse Act cases to paint a picture of the sort of computer-enabled criminals who not only plagued Great Britain's digital doings in the 21st Century but were also caught by the plod. The average Computer Misuse Act convict is likely to be a semi- or low-skilled individual, mostly working alone and more likely than not to have no knowledge of his or her victim, James Crawford of Royal Holloway, University of London, found.

An academic researcher has analysed more than 100 Computer Misuse Act cases to paint a picture of the sort of computer-enabled criminals who not only plagued Great Britain's digital doings in the 21st Century but were also caught by the plod. The average Computer Misuse Act convict is likely to be a semi- or low-skilled individual, mostly working alone and more likely than not to have no knowledge of his or her victim, James Crawford of Royal Holloway, University of London, found.

Behind the strategies and solutions needed to counter today's cyber threats are-dedicated cybersecurity researchers. What drives these specialists? To understand the motivations for why these cybersecurity pros do what they do, we decided to talk with cybersecurity analysts from around the world.

Pwn2Own 2021 ended with contestants earning a record $1,210,000 for exploits and exploits chains demoed over the course of three days. The total prize pool for Pwn2Own 2021 was over $1,500,000 in cash and included a Tesla Model 3.
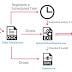
An Iranian threat actor has unleashed a new cyberespionage campaign against a possible Lebanese target with a backdoor capable of exfiltrating sensitive information from compromised systems. Cybersecurity firm Check Point attributed the operation to APT34, citing similarities with previous techniques used by the threat actor as well as based on its pattern of victimology.

A researcher has disclosed the details of a series of vulnerabilities that could have been exploited by an attacker to access an organization's private pages on GitHub. GitHub Pages is a service that individuals and organizations can use to host websites.

The same North Korean threat actors that targeted security researchers in January appear to be readying a new campaign using a fake company that aim to lure security professionals into another cyber-espionage trap. While researchers have seen no evidence yet of nefarious activity from attackers that leverage these web assets, it appears that attackers are gearing up to target security researchers again by the nature of the activity, according to Google TAG. Like previous websites that Google TAG has observed Zinc establish, the SecuriElite website has a link to the group's PGP public key at the bottom of the page, researchers noted.