Security News

A suspected Chinese threat actor targeted a large U.S. organization earlier this year as part of a four-month-long intrusion. According to Broadcom-owned Symantec, the first evidence of the...
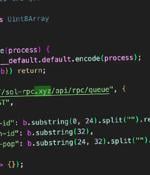
Cybersecurity researchers are alerting to a software supply chain attack targeting the popular @solana/web3.js npm library that involved pushing two malicious versions capable of harvesting users'...

The first UEFI bootkit specifically targeting Linux systems has been discovered, marking a shift in stealthy and hard-to-remove bootkit threats that previously focused on Windows. [...]

ESET Research has discovered the first UEFI bootkit designed for Linux systems, named Bootkitty by its creators. Researchers believe this bootkit is likely an initial proof of concept, and based...

Cybersecurity researchers have shed light on what has been described as the first Unified Extensible Firmware Interface (UEFI) bootkit designed for Linux systems. Dubbed Bootkitty by its creators...

Researchers have discovered vulnerabilities in the update process of Palo Alto Networks (CVE-2024-5921) and SonicWall (CVE-2024-29014) corporate VPN clients that could be exploited to remotely...
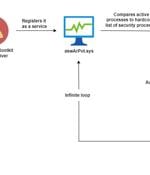
Cybersecurity researchers have uncovered a new malicious campaign that leverages a technique called Bring Your Own Vulnerable Driver (BYOVD) to disarm security protections and ultimately gain...

ESET researchers have identified multiple samples of two previously unknown Linux backdoors: WolfsBane and FireWood. The goal of the backdoors and tools discovered is cyberespionage that targets...

GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and...

Cybersecurity researchers have disclosed two security flaws in Google's Vertex machine learning (ML) platform that, if successfully exploited, could allow malicious actors to escalate privileges...