Security News

A now-patched vulnerability affecting Oracle VM VirtualBox could be potentially exploited by an adversary to compromise the hypervisor and cause a denial-of-service condition. "Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox," the advisory reads.

A team of Italian researchers has compiled a set of three attacks called 'Printjack,' warning users of the significant consequences of over-trusting their printer. The first type of Printjack attack is to recruit the printer in a DDoS swarm, and threat actors can do this by exploiting a known RCE vulnerability with a publicly available PoC. The researchers use CVE-2014-3741 as an example but underline that at least a few dozen other vulnerabilities are available in the MITRE database.

"Based on intelligence garnered from the Arkose Labs Network, we predict a 60 percent increase in attacks for the upcoming 2021 holiday shopping season. No digital business is immune to this threat." It is estimated that eight million attacks will occur daily during the 2021 holiday shopping season that is now underway.

How widespread is the use of hidden root CAs and certificates signed by them? To answer that and other questions, a group of researchers from several Chinese and U.S. universities and Qihoo 360, the company developing the 360 Secure Browser, have collected 5 months worth of certificate data from volunteer users and analyzed certificate chains and verification statuses in web visits. Many flaws in the implementation of hidden root CAs and certificates.
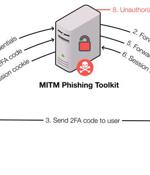
The findings come from a new study undertaken by a group of researchers from Stony Brook University and Palo Alto Networks, who have demonstrated a new fingerprinting technique that makes it possible to identify MitM phishing kits in the wild by leveraging their intrinsic network-level properties, effectively automating the discovery and analysis of phishing websites. Dubbed "PHOCA" - named after the Latin word for "Seals" - the tool not only facilitates the discovery of previously unseen MitM phishing toolkits, but also be used to detect and isolate malicious requests coming from such servers.
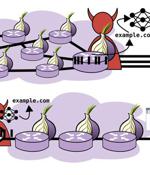
A new analysis of website fingerprinting attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. Tor browser offers "Unlinkable communication" to its users by routing internet traffic through an overlay network, consisting of more than six thousand relays, with the goal of anonymizing the originating location and usage from third parties conducting network surveillance or traffic analysis.

Lazarus, the North Korea-affiliated state-sponsored group, is attempting to once again target security researchers with backdoors and remote access trojans using a trojanized pirated version of the popular IDA Pro reverse engineering software. The findings were reported by ESET security researcher Anton Cherepanov last week in a series of tweets.

The balance between hands-free payments and the security standards required to protect those transactions has tipped too far in the wrong direction, according to a security expert. At a session at Black Hat Europe 2021 this week, Timur Yunusov, a senior security expert at Positive Technologies, explained flaws in contactless payment apps that could lead to fraud using lost or stolen mobile phones.

A new cyber mercenary hacker-for-hire group dubbed "Void Balaur" has been linked to a string of cyberespionage and data theft activities targeting thousands of entities as well as human rights activists, politicians, and government officials around the world at least since 2015 for financial gain while lurking in the shadows. "The group does not try to wriggle out of a difficult position by justifying its business, nor is it involved in lawsuits against anybody attempting to report on their activities. Instead, this group is quite open about what it does: breaking into email accounts and social media accounts for money," Hacquebord added.

A team of researchers at the Imperial College in London have presented a simple method to evade detection by image content scanning mechanisms, such as Apple's CSAM. CSAM was a controversial proposal submitted by Apple earlier this year. The research presented at the recent USENIX Security Symposium by British researchers shows that neither Apple's CSAM nor any system of this type would effectively detect illegal material.