Security News

ThreatLocker has created a list of the top 15 actions to secure an organization if employing a remote or hybrid workforce. Learn more in this free e-book from ThreatLocker. [...]

Two security vulnerabilities have been disclosed in the open-source Traccar GPS tracking system that could be potentially exploited by unauthenticated attackers to achieve remote code execution...

SAP has released its security patch package for August 2024, addressing 17 vulnerabilities, including a critical authentication bypass that could allow remote attackers to fully compromise the...
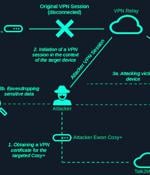
Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks. The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in configuration files, and even get correctly signed X.509 VPN certificates for foreign devices to take over their VPN sessions.
Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users. Successful exploitation of one of these flaws could allow a remote attacker to obtain covert audio capture from Sonos devices by means of an over-the-air attack.

UK-based mobile device management vendor Mobile Guardian has admitted that on August 4 it suffered a security incident that involved unauthorized access to iOS and ChromeOS devices managed by its tools. Mobile Guardian focuses on the education sector - offering device management, web filtering, and classroom management tools.
A new zero-day pre-authentication remote code execution vulnerability has been disclosed in the Apache OFBiz open-source enterprise resource planning system that could allow threat actors to achieve remote code execution on affected instances. "The root cause of the vulnerability lies in a flaw in the authentication mechanism," SonicWall, which discovered and reported the shortcoming, said in a statement.

Researchers are warning of threat actors increasingly abusing the Cloudflare Tunnel service in malware campaigns that usually deliver remote access trojans (RATs). [...]

Geyer also addresses the challenges and solutions for securing remote access to critical OT assets. The trend of connecting previously isolated OT assets to public networks is driven by several factors, including the need for real-time data analysis, remote management, operational efficiency, and improved decision-making.

Microsoft Outlook can be turned into a C2 beacon to remotely execute code, as demonstrated by a new red team post-exploitation framework named "Specula," released today by cybersecurity firm TrustedSec. This C2 framework works by creating a custom Outlook Home Page using WebView by exploiting CVE-2017-11774, an Outlook security feature bypass vulnerability patched in October 2017.