Security News
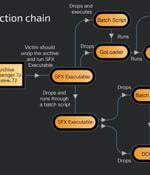
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to deliver DarkCrystal RAT (aka DCRat) and a previously...

Details have emerged about a now-patched security flaw in Styra's Open Policy Agent (OPA) that, if successfully exploited, could have led to leakage of New Technology LAN Manager (NTLM) hashes....

Microsoft says this month's Patch Tuesday cumulative updates fix a known issue that causes Windows servers to disrupt Remote Desktop connections in enterprise networks after installing the July...

A critical security flaw has been disclosed in the Apache Avro Java Software Development Kit (SDK) that, if successfully exploited, could allow the execution of arbitrary code on susceptible...

With 14 serious security flaws found, what a gift for spies and crooks Fourteen bugs in DrayTek routers — including one critical remote-code-execution flaw that received a perfect 10 out of 10...

Only 2 out of 5 tested products were equitable across demographics A study by the US General Services Administration (GSA) has revealed that five remote identity verification (RiDV) technologies...

Critical security vulnerabilities have been disclosed in six different Automatic Tank Gauge (ATG) systems from five manufacturers that could expose them to remote attacks. "These vulnerabilities...

A new set of security vulnerabilities has been disclosed in the OpenPrinting Common Unix Printing System (CUPS) on Linux systems that could permit remote command execution under certain...

Under certain conditions, attackers can chain a set of vulnerabilities in multiple components of the CUPS open-source printing system to execute arbitrary code remotely on vulnerable machines. [...]

No patches yet, can be mitigated, requires user interaction Final update After days of anticipation, what was billed as one or more critical unauthenticated remote-code execution vulnerabilities...