Security News

Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions."This vulnerability allows a remote attacker to potentially execute arbitrary commands on vulnerable OpenSSH's forwarded ssh-agent," Saeed Abbasi, manager of vulnerability research at Qualys, said in an analysis last week.

Two more security flaws have been disclosed in AMI MegaRAC Baseboard Management Controller software that, if successfully exploited, could allow threat actors to remotely commandeer vulnerable servers and deploy malware. "These new vulnerabilities range in severity from High to Critical, including unauthenticated remote code execution and unauthorized device access with superuser permissions," Eclypsium researchers Vlad Babkin and Scott Scheferman said in a report shared with The Hacker News.

TechRepublic Premium Checklist: How to Create a Team Charter A good team charter should define the purpose of a team, how work will get done and the expected outcomes. Often, a team charter is described as a "Roadmap" for the team and its sponsors.

The U.S. Cybersecurity and Infrastructure Security Agency has alerted of two security flaws impacting Rockwell Automation ControlLogix EtherNet/IP communication module models that could be exploited to achieve remote code execution and denial-of-service. "The results and impact of exploiting these vulnerabilities vary depending on the ControlLogix system configuration, but they could lead to denial or loss of control, denial or loss of view, theft of operational data, or manipulation of control for disruptive or destructive consequences on the industrial process for which the ControlLogix system is responsible," Draogos said.
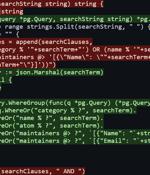
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution on vulnerable systems. "These SQL injections happened despite the use of an Object-Relational Mapping library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "Misconfiguration of the database."

Cybersecurity solutions company Fortinet has updated its zero-trust access solution FortiNAC to address a critical-severity vulnerability that attackers could leverage to execute code and commands. FortiNAC is a allows organizations to manage network-wide access policies, gain visibility of devices and users, and secure the network against unauthorized access and threats.
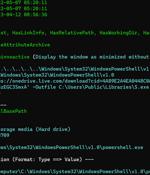
A new phishing campaign codenamed MULTI#STORM has set its sights on India and the U.S. by leveraging JavaScript files to deliver remote access trojans on compromised systems. The multi-stage attack chain commences when an email recipient clicks the embedded link pointing to a password-protected ZIP file hosted on Microsoft OneDrive with the password "12345."

The Syxsense Synergy event last week featured a range of analysts, end users and company spokespeople with a central theme of the convergence of endpoint management and security - two areas that have traditionally remained apart. "That's why there is a growing need for the convergence of the security and endpoint management groups within organizations to address attack surface management, vulnerability protection and automated remediation."

A cyberespionage and hacking campaign tracked as 'RedClouds' uses the custom 'RDStealer' malware to automatically steal data from drives shared through Remote Desktop connections. The Remote Desktop Protocol is a proprietary Microsoft protocol that allows users to remotely connect to Windows desktops and use them as if they were in front of the computer.

We'll examine the impact of the shifting role of data centers on network strategies, the implementation of a zero-trust security framework, and how 5G networks might further decentralize workplaces. Historically businesses have relied on remote access VPNs to allow remote employees to access applications and services on their corporate network.