Security News

A widely used Windows-only utility, WinRAR can create and extract file archives in various compression formats. CVE-2023-40477 is a remote code execution vulnerability that could allow remote threat actors to execute arbitrary code on an affected WinRAR installation.

Networking hardware company Juniper Networks has released an "Out-of-cycle" security update to address multiple flaws in the J-Web component of Junos OS that could be combined to achieve remote code execution on susceptible installations. They affect all versions of Junos OS on SRX and EX Series.

Two stack-based buffer overflow bugs have been discovered in Ivanti Avalanche, an enterprise mobility management solution. Ivanti released Avalanche version 6.4.1 security update on August 3, 2023, which also fixes additional RCE and authentication bypass vulnerabilities.

Four security vulnerabilities in the ScrutisWeb ATM fleet monitoring software made by Iagona could be exploited to remotely break into ATMs, upload arbitrary files, and even reboot the terminals. The issues have been addressed in ScrutisWeb version 2.1.38.
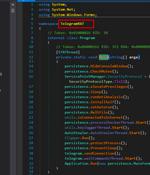
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

A set of 15 high-severity security flaws have been disclosed in the CODESYS V3 software development kit that could result in remote code execution and denial-of-service under specific conditions, posing risks to operational technology environments. "Exploitation of the discovered vulnerabilities, which affect all versions of CODESYS V3 prior to version 3.5.19.0, could put operational technology infrastructure at risk of attacks, such as remote code execution and denial-of-service," Vladimir Tokarev of the Microsoft Threat Intelligence Community said in a report.

"The report shows 92% of survey respondents recognize the importance of adopting a zero trust architecture; however, it is concerning to see many organizations are still using a VPN for remote employee and third-party access, inadvertently providing a juicy attack surface for threat actors," said Deepen Desai, Global CISO and Head of Security Research, Zscaler. "Legacy firewall and VPN vendors are spinning virtual VPNs in the cloud and claiming that it is zero trust, and they go the extra length to hide the word"VPN". Customers need to ask the right questions to make sure that they are not getting a false sense of security with these virtualized legacy offerings in the cloud. In order to safeguard against evolving ransomware attacks, it is critical for organizations to eliminate the use of VPNs, prioritize user-to-app segmentation, and implement an in-line contextual data loss prevention engine with full TLS inspection," added Desai.

Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud (EC2) instances (virtual servers), as well as...
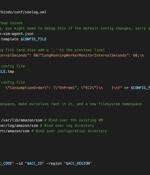
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments. "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.
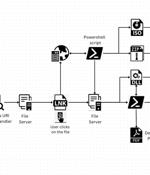
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT. The novel attack technique, per Trellix, takes advantage of the "Search-ms:" URI protocol handler, which offers the ability for applications and HTML links to launch custom local searches on a device, and the "Search:" application protocol, a mechanism for calling the desktop search application on Windows. It's worth noting that clicking on the link also generates a warning "Open Windows Explorer?," approving which "The search results of remotely hosted malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results," the researchers explained.