Security News
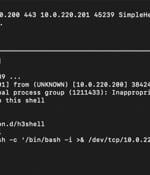
Cybersecurity researchers have disclosed multiple security flaws in SimpleHelp remote access software that could lead to information disclosure, privilege escalation, and remote code execution....

Threat actors are exploiting a critical remote command execution vulnerability, tracked as CVE-2024-50603, in Aviatrix Controller instances to install backdoors and crypto miners. [...]

Threat actors are attempting to take advantage of a recently disclosed security flaw impacting GFI KerioControl firewalls that, if successfully exploited, could allow malicious actors to achieve...

3 CVEs added to CISA's catalog Cybercriminals are actively exploiting two vulnerabilities in Mitel MiCollab, including a zero-day flaw – and a critical remote code execution vulnerability in...

The Apache Software Foundation (ASF) has released patches to address a maximum severity vulnerability in the MINA Java network application framework that could result in remote code execution...

The Apache Software Foundation (ASF) has released a security update to address an important vulnerability in its Tomcat server software that could result in remote code execution (RCE) under...

More details released after devs allowed weeks to apply fixes We now know the remote code execution vulnerability in Apache Struts 2 disclosed back in November carries a near-maximum severity...

Hackers are actively exploiting a zero-day vulnerability in Cleo managed file transfer software to breach corporate networks and conduct data theft attacks. [...]

Researchers have published a proof-of-concept (PoC) exploit for CVE-2024-8785, a critical remote code execution vulnerability affecting Progress WhatsUp Gold, a popular network monitoring solution...

Veeam has released security updates to address a critical flaw impacting Service Provider Console (VSPC) that could pave the way for remote code execution on susceptible instances. The...