Security News

Threat actors have observed the increasingly common ClickFix technique to deliver a remote access trojan named NetSupport RAT since early January 2025. NetSupport RAT, typically propagated via...

Cybersecurity researchers have shed light on a new remote access trojan called NonEuclid that allows bad actors to remotely control compromised Windows systems. "The NonEuclid remote access trojan...
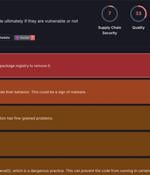
Cybersecurity researchers have discovered a malicious package on the npm package registry that masquerades as a library for detecting vulnerabilities in Ethereum smart contracts but, in reality,...
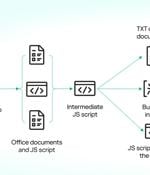
A newly discovered malware campaign has been found to target private users, retailers, and service businesses mainly located in Russia to deliver NetSupport RAT and BurnsRAT. The campaign, dubbed...

A newly patched security flaw impacting Windows NT LAN Manager (NTLM) was exploited as a zero-day by a suspected Russia-linked actor as part of cyber attacks targeting Ukraine. The vulnerability...

Cybersecurity researchers have discovered a new phishing campaign that spreads a new fileless variant of known commercial malware called Remcos RAT. Remcos RAT "provides purchases with a wide...
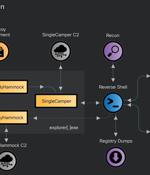
The Russian threat actor known as RomCom has been linked to a new wave of cyber attacks aimed at Ukrainian government agencies and unknown Polish entities since at least late 2023. The intrusions...

Cybersecurity researchers have disclosed a new malware campaign that leverages a malware loader named PureCrypter to deliver a commodity remote access trojan (RAT) called DarkVision RAT. The...
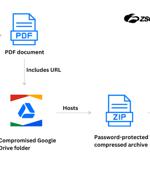
The Colombian insurance sector is the target of a threat actor tracked as Blind Eagle with the end goal of delivering a customized version of a known commodity remote access trojan (RAT) known as...

Users of Chinese instant messaging apps like DingTalk and WeChat are the target of an Apple macOS version of a backdoor named HZ RAT. The artifacts "almost exactly replicate the functionality of...