Security News

A proof-of-concept (PoC) exploit for four critical Ivanti Endpoint Manager vulnerabilities has been released by Horizon3.ai researchers. The vulnerabilities – CVE-2024-10811, CVE-2024-13161,...

Attackers are now targeting an authentication bypass vulnerability affecting SonicWall firewalls shortly after the release of proof-of-concept (PoC) exploit code. [...]

Palo Alto Networks has fixed a high-severity authentication bypass vulnerability (CVE-2025-0108) in the management web interface of its next-gen firewalls, a proof-of-concept exploit (PoC) for...

Cisco has released patches for a critical privilege escalation vulnerability in Meeting Management (CVE-2025-20156) and a heap-based buffer overflow flaw (CVE-2025-20128) that, when triggered,...

Cisco has released security updates to patch a ClamAV denial-of-service (DoS) vulnerability, which has proof-of-concept (PoC) exploit code. [...]
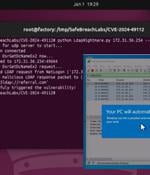
A proof-of-concept (PoC) exploit has been released for a now-patched security flaw impacting Windows Lightweight Directory Access Protocol (LDAP) that could trigger a denial-of-service (DoS)...

Adobe has released out-of-band security updates to address a critical ColdFusion vulnerability with proof-of-concept exploit code. [...]

A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000...

Still unpatched 100+ days later, watchTowr says A zero-day arbitrary file read vulnerability in Mitel MiCollab can be chained with a now-patched critical bug in the same platform to give attackers...

A zero-day vulnerability in the Mitel MiCollab enterprise collaboration suite can be exploited to read files containing sensitive data, watchTowr researcher Sonny Macdonald has disclosed, and...