Security News
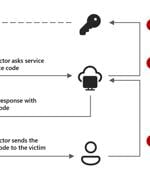
Microsoft is calling attention to an emerging threat cluster it calls Storm-2372 that has been attributed to a new set of cyber attacks aimed at a variety of sectors since August 2024. The attacks...

An attempt to block a phishing URL in Cloudflare's R2 object storage platform backfired yesterday, triggering a widespread outage that brought down multiple services for nearly an hour. [...]

Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.

And you, China, Russia, North Korea ... Guardrails block malware generation Google says it's spotted Chinese, Russian, Iranian, and North Korean government agents using its Gemini AI for nefarious...

Microsoft reminded Microsoft 365 admins that its new brand impersonation protection feature for Teams Chat will be available for all customers by mid-February 2025. [...]

For the APAC region as a whole, credential phishing attacks rose by 30.5% between 2023 and 2024.

Ransomware gangs are increasingly adopting email bombing followed by posing as tech support in Microsoft Teams calls to trick employees into allowing remote control and install malware that...

Cybersecurity researchers have detailed a new adversary-in-the-middle (AitM) phishing kit that's capable of Microsoft 365 accounts with an aim to steal credentials and two-factor authentication...

FSB cyberspies venture into a new app for espionage, Microsoft says Star Blizzard, a prolific phishing crew backed by the Russian Federal Security Service (FSB), conducted a new campaign aiming to...

The Russian threat actor known as Star Blizzard has been linked to a new spear-phishing campaign that targets victims' WhatsApp accounts, signaling a departure from its longstanding tradecraft in...