Security News

Phishing attacks using open redirect flaws are on the rise again, according to Kroll's Cyber Threat Intelligence team, which means organizations should consider refreshing employees' awareness and knowledge on how to spot them. Open redirect vulnerabilities in web applications allows threat actors to manipulate legitimate URLs to redirect victims to an external malicious URL. "They occur when a website allows for user-supplied input as part of a URL parameter in a redirect link, without proper validation or sanitization," says George Glass, Kroll's Head of Threat Intelligence.

A phishing campaign using QR codes has been detected targeting various industries, with the aim to acquire Microsoft credentials. "The most notable target, a major Energy company based in the US, saw about 29% of the over 1000 emails containing malicious QR codes. Other top 4 targeted industries include Manufacturing, Insurance, Technology, and Financial Services seeing 15%, 9%, 7%, and 6% of the campaign traffic respectively," said Nathaniel Raymond, cyber threat intelligence analyst at Cofense.

A sophisticated Facebook phishing campaign has been observed exploiting a zero-day flaw in Salesforce's email services, allowing threat actors to craft targeted phishing messages using the company's domain and infrastructure. What makes the attack notable is that the phishing kit is hosted as a game under the Facebook apps platform using the domain apps.
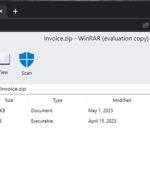
A new phishing technique called "File archiver in the browser" can be leveraged to "Emulate" a file archiver software in a web browser when a victim visits a.ZIP domain. Threat actors, in a nutshell, could create a realistic-looking phishing landing page using HTML and CSS that mimics legitimate file archive software, and host it on a.zip domain, thus elevating social engineering campaigns.

Phishers are using encrypted restricted-permission messages attached in phishing emails to steal Microsoft 365 account credentials. "The initial emails are sent from compromised Microsoft 365 accounts and appear to be targeted towards recipient addresses where the sender might be familiar."

Phishers are looking to trick owners of Facebook pages with fake notices from the social network, in an attempt to get them to part with sensitive information. Such a link makes it less likely that email security solutions will flag the email as potentially malicious, and can also give a false sense of security to the potential targets, as the email ostensibly came from Facebook and contains a link to a page hosted on Facebook.

Group-IB has discovered that the recently disclosed phishing attacks on the employees of Twilio and Cloudflare were part of the massive phishing campaign that resulted in 9,931 accounts of over 130 organizations being compromised. Group-IB Threat Intelligence team uncovered and analyzed the attackers' phishing infrastructure, including phishing domains, the phishing kit as well as the Telegram channel controlled by the threat actors to drop compromised information.

Threat actors are making their way around two-factor authentication and using other clever evasion tactics in a recently observed phishing campaign aimed at taking over Coinbase accounts to defraud users of their crypto balances. Attackers employ a range of tactics to avoid detection, including one researchers call "Short lived domains"-in which the domains used in the attack "Stay alive for extremely short periods of time"-that deviates from typical phishing practices, researchers wrote.

An ongoing, large-scale phishing campaign is targeting owners of business email accounts at companies in the FinTech, Lending, Insurance, Energy and Manufacturing sectors in the US, UK, New Zealand and Australia, Zscaler researchers are warning. The attackers are using a variety of tecniques and tactics to evade corporate email security solutions and a custom phishing kit that allows them to bypass multi-factor authentication protection to hijack enterprise Microsoft accounts.

A massive phishing campaign has been targeting Office 365 users in over 10,000 organizations since September 2021 and successfully bypassing multi-factor authentication set up to protect the accounts. The attackers use proxy servers and phishing websites to steal users' password and session cookie.