Security News

The popularity of Brazil's PIX instant payment system has made it a lucrative target for threat actors looking to generate illicit profits using a new malware called GoPIX. Kaspersky, which has...

China-based scammers are using a combination of fake loan apps and India's real-time mobile payment system, Unified Payments Interface, to separate victims from their cash, according to a report by threat intel firm CloudSEK. "UPI service providers currently operate without coverage under the Prevention of Money Laundering Act," explained [PDF] CloudSEK researchers, letting the scammers' exploit the platforms with relative ease. Chinese payment gateways ensure the authorities cannot pursue the scammers.
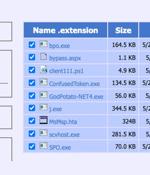
A financially motivated campaign has been targeting online payment businesses in the Asia Pacific, North America, and Latin America with web skimmers for more than a year. The BlackBerry Research...

Caesars Entertainment, self-described as the largest U.S. casino chain with the most extensive loyalty program in the industry, says it paid a ransom to avoid the online leak of customer data stolen in a recent cyberattack. Caesars' 8-K also implies that a ransom demanded by the attackers was paid to prevent the leak of the stolen data online-a Wall Street Journal report says the hotel and casino entertainment company paid roughly $15 million, half of the attackers' initial $30 million demand.

AI Spera is pleased to announce its attainment of the highest global compliance certification level, PCI DSS Level 1 for Criminal IP, its in-house developed and serviced Cyber Threat Intelligence search engine. The Payment Card Industry Data Security Standard is a global information security standard designed to safeguard card payment information and transactions.

Threat actors continued to exploit technical misconfigurations through various fraud schemes, according to a new report from Visa. While the global fraud rate trended lower than normal expected fraud levels during the report's time period, Visa shared that it helped to proactively block $30 billion in those time periods.

Purfoods has notified more than 1.2 million people that their personal and medical data - including payment card and bank account numbers, security codes, and some protected health information - may have been stolen from its servers during what sounds like a ransomware infection earlier this year. According to documents filed with the Maine Attorney General's office and a notification letter mailed to 1,237,681 individuals, criminals broke into Purfoods' network in January 16, encrypted some files containing customer information, and may have stolen others.

Ransomware remains a lucrative tool for cybercriminals as attackers continue to target a wide array of businesses. In response to this growing threat, an increasing number of organizations are compelled to meet ransom demands, perceiving it as their only viable course of action.
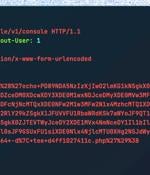
Threat actors are actively exploiting a recently disclosed critical security flaw in the WooCommerce Payments WordPress plugin as part of a massive targeted campaign. "Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023," Wordfence security researcher Ram Gall said in a Monday post.

Hackers are conducting widespread exploitation of a critical WooCommerce Payments plugin to gain the privileges of any users, including administrators, on vulnerable WordPress installation. WooCommerce Payments is a very popular WordPress plugin allowing websites to accept credit and debit cards as payment in WooCommerce stores.