Security News

Ai researchers have published some details about CVE-2023-39143, two vulnerabilities in PaperCut application servers that could be exploited by unauthenticated attackers to execute code remotely. They noted, unlike the PaperCut vulnerability recently leveraged by Clop and LockBit ransomware affiliates, CVE-2023-39143 is not a "One-shot" RCE bug.

Cybersecurity researchers have discovered a new high-severity security flaw in PaperCut print management software for Windows that could result in remote code execution under specific circumstances. Tracked as CVE-2023-39143, the flaw impacts PaperCut NG/MF prior to version 22.1.3.

PaperCut recently fixed a critical security vulnerability in its NG/MF print management software that allows unauthenticated attackers to gain remote code execution on unpatched Windows servers. While it only impacts servers in non-default configurations where the external device integration setting is toggled, Horizon3 said in a report published on Friday that most Windows PaperCut servers have it enabled.

Several ransomware groups and state-sponsored cyberespionage threat actors are exploiting a vulnerability affecting printing software tools PaperCut MF and PaperCut NG to compromise their targets. The new PaperCut vulnerability, CVE-2023-27350, affects different PaperCut MF and PaperCut NG software, allowing an attacker to bypass authentication and execute arbitrary code with SYSTEM privileges.

The FBI and CISA issued a joint advisory to warn that the Bl00dy Ransomware gang is now also actively exploiting a PaperCut remote-code execution vulnerability to gain initial access to networks. "In early May 2023, according to FBI information, the Bl00dy Ransomware Gang gained access to victim networks across the Education Facilities Subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the internet," reads the security advisory.

U.S. cybersecurity and intelligence agencies have warned of attacks carried out by a threat actor known as the Bl00dy Ransomware Gang that attempt to exploit vulnerable PaperCut servers against the education facilities sector in the country. "The Bl00dy Ransomware Gang gained access to victim networks across the Education Facilities Subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the internet," the agencies said.
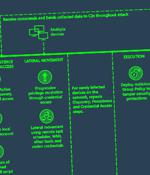
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft said. The tech giant's threat intelligence team said it observed both Mango Sandstorm and Mint Sandstorm weaponizing CVE-2023-27350 in their operations to achieve initial access.

Microsoft says Iranian state-backed hackers have joined the ongoing assault targeting vulnerable PaperCut MF/NG print management servers. "The PaperCut exploitation activity by Mint Sandstorm appears opportunistic, affecting organizations across sectors and geographies," the Microsoft Threat Intelligence team said.

A new proof-of-concept exploit for an actively exploited PaperCut vulnerability was released that bypasses all known detection rules. The PaperCut vulnerability, tracked as CVE-2023-27350, is a critical severity unauthenticated remote code execution flaw in PaperCut MF or NG versions 8.0 or later that has been exploited in ransomware attacks.
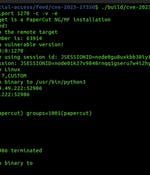
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350, the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.