Security News

Though cybersecurity is on every executive's checklist today, most struggle with growing compliance burdens, keeping the costs moderate and bringing team alignment. Read this guide, written by Avya Chaudhary for TechRepublic Premium, to learn how to perform a cybersecurity assessment within a five-point framework.

The purpose of this customizable Social Engineering Awareness Policy, written by Maria Carrisa Sanchez for TechRepublic Premium, is to provide guidelines for preventing, recognizing and addressing social engineering attacks. Regular update of passwords: The company believes passwords serve as the fundamental line of security against unwanted access.

A joint advisory from international cybersecurity agencies and law enforcement warns of the tactics used by the Chinese state-sponsored APT 40 hacking group and their hijacking of SOHO routers to launch cyberespionage attacks. Previously, APT40 was linked to a wave of attacks targeting over 250,000 Microsoft Exchange servers using the ProxyLogon vulnerabilities and campaigns involving exploiting flaws in widely used software, such as WinRAR. APT40 activity overview.

Evolve Bank & Trust (Evolve) is sending notices of a data breach to 7.6 million Americans whose data was stolen during a recent LockBit ransomware attack. [...]

Certificate Watch Demonstrating that Microsoft is not alone in its inability to keep track of certificates is UK power market biz Elexon. Elexon is an important cog in the UK's wholesale electricity market machine and provides operational data via its Insight Solution platform.

Evolve Bank & Trust says the data of more than 7.6 million customers was stolen during the LockBit break-in in late May, per a fresh filing with Maine's attorney general. It's the first time Evolve has confirmed the scale of the data theft - which affected at least three of its major partners, past and present - and it expects the number to rise as its investigations continue.

Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle attacks and bypass integrity checks under certain circumstances. "The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks," InkBridge Networks CEO Alan DeKok, who is the creator of the FreeRADIUS Project, said in a statement.

Lookout discovered GuardZoo, Android spyware targeting Middle Eastern military personnel. Based on application lures, targeting, and threat actor-controlled server locations, Lookout attributes GuardZoo to a Yemeni, Houthi-aligned threat actor.

A new critical security vulnerability in the RADIUS protocol, dubbed BlastRADIUS, leaves most networking equipment open to Man-in-the-Middle attacks. To protect businesses from BlastRADIUS, "Every network switch, router, firewall, VPN concentrator, access point, and DSL gateway worldwide needs to be updated to add integrity and authentication checks for these packets," explains Alan DeKok, CEO of InkBridge Networks and one of the foremost experts on RADIUS servers.
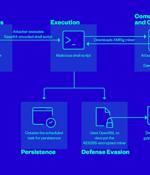
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.