Security News

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 has been using this tool to exploit the CVE-2022-38028 vulnerability "Since at least June 2020 and possibly as early as April 2019.".

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 designed this tool to target the CVE-2022-38028 vulnerability reported by the U.S. National Security Agency, which Redmond fixed during the Microsoft October 2022 Patch Tuesday.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The tech world has a problem: Security fragmentation. There's no standard set of rules or even language for mitigating cyber risk used to address the growing threats of hackers, ransomware and stolen data, and the threat to data only continues to grow.

Threats from malware, cryptographic infections and compromised networks have never been greater. Companies can't protect their technological infrastructure without a solid grasp of the actual equipment in play.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Synlab Italia has suspended all its medical diagnostic and testing services after a ransomware attack forced its IT systems to be taken offline.Part of the Synlab group that is present in 30 countries worldwide, the Synlab Italia network operates 380 labs and medical centers across Italy.

The attacker is exploiting a property of GitHub: comments to a particular repo can contain files, and those files will be associated with the project in the URL. What this means is that someone can upload malware and "Attach" it to a legitimate and trusted project. As the file's URL contains the name of the repository the comment was created in, and as almost every software company uses GitHub, this flaw can allow threat actors to develop extraordinarily crafty and trustworthy lures.
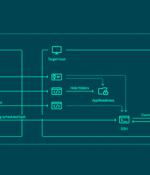
The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky...

BleepingComputer recently reported how a GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with Microsoft repositories, making the files appear trustworthy. While most of the malware-associated activity was based around the Microsoft GitHub URLs, this "Flaw" could be abused with any public repository on GitHub or GitLab, allowing threat actors to create very convincing lures.