Security News

State-backed hackers from North Korea are conducting ransomware attacks against healthcare and critical infrastructure facilities to fund illicit activities, U.S. and South Korean cybersecurity and intelligence agencies warned in a joint advisory. This includes "Cyber operations targeting the United States and South Korea governments - specific targets include Department of Defense Information Networks and Defense Industrial Base member networks," the authorities said.

A new cyber espionage campaign dubbed 'No Pineapple!' has been attributed to the North Korean Lazarus hacking group, allowing the threat actors to stealthily steal 100GB of data from the victim without causing any destruction. The campaign is named after the '' error seen transmitted by a remote access malware when uploading stolen data to the threat actor's servers.

A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems. Targets of the malicious operation included a healthcare research organization in India, the chemical engineering department of a leading research university, as well as a manufacturer of technology used in the energy, research, defense, and healthcare sectors, suggesting an attempt to breach the supply chain.

A North Korean nation-state group notorious for crypto heists has been attributed to a new wave of malicious email attacks as part of a "Sprawling" credential harvesting activity targeting a number of industry verticals, marking a significant shift in its strategy. The state-aligned threat actor is being tracked by Proofpoint under the name TA444, and by the larger cybersecurity community as APT38, BlueNoroff, Copernicium, and Stardust Chollima.

The FBI has confirmed that the North Korean state-sponsored 'Lazarus' and APT38 hacking groups were behind the theft of $100 million worth of Ethereum stolen from Harmony Horizon in June 2022. Yesterday, the FBI confirmed that two North Korean hacking groups, Lazarus and APT38, were behind the attack.

The U.S. Federal Bureau of Investigation on Monday confirmed that North Korean threat actors were responsible for the theft of $100 million in cryptocurrency assets from Harmony Horizon Bridge in June 2022. The law enforcement agency attributed the hack to the Lazarus Group and APT38, the latter of which is a North Korean state-sponsored threat group that specializes in financial cyber operations.
The Lazarus Group threat actor has been observed leveraging fake cryptocurrency apps as a lure to deliver a previously undocumented version of the AppleJeus malware, according to new findings from Volexity. "This activity notably involves a campaign likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by way of malicious Microsoft Office documents," researchers Callum Roxan, Paul Rascagneres, and Robert Jan Mora said.
Hackers tied to the North Korean government have been observed using an updated version of a backdoor known as Dtrack targeting a wide range of industries in Germany, Brazil, India, Italy, Mexico, Switzerland, Saudi Arabia, Turkey and the U.S. "Dtrack allows criminals to upload, download, start or delete files on the victim host," Kaspersky researchers Konstantin Zykov and Jornt van der Wiel said in a report. Discovered in September 2019, the malware has been previously deployed in a cyber attack aimed at a nuclear power plant in India, with more recent intrusions using Dtrack as part of Maui ransomware attacks.

North Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and Latin America. In the new campaign, Kaspersky has seen DTrack distributed using filenames commonly associated with legitimate executables.
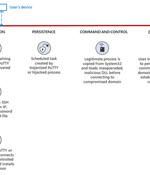
A "Highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022. Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.