Security News

Lazarus, the North Korea-affiliated state-sponsored group, is attempting to once again target security researchers with backdoors and remote access trojans using a trojanized pirated version of the popular IDA Pro reverse engineering software. The findings were reported by ESET security researcher Anton Cherepanov last week in a series of tweets.

Lazarus Group, the advanced persistent threat group attributed to the North Korean government, has been observed waging two separate supply chain attack campaigns as a means to gain a foothold into corporate networks and target a wide range of downstream entities. The latest intelligence-gathering operation involved the use of MATA malware framework as well as backdoors dubbed BLINDINGCAN and COPPERHEDGE to attack the defense industry, an IT asset monitoring solution vendor based in Latvia, and a think tank located in South Korea, according to a new Q3 2021 APT Trends report published by Kaspersky.

North Korean-sponsored Lazarus hacking group has switched focus on new targets and was observed by Kaspersky security researchers expanding its supply chain attack capabilities. Lazarus used a new variant of the BLINDINGCAN backdoor to target a South Korean think tank in June after deploying it to breach a Latvian IT vendor in May. "In the first case discovered by Kaspersky researchers, Lazarus developed an infection chain that stemmed from legitimate South Korean security software deploying a malicious payload," the researchers said.

Security researchers piecing together evidence from multiple attacks on cryptocurrency exchanges, attributed to a threat actor they named CryptoCore have established a strong connection to the North Korean state-sponsored group Lazarus. Last year, cybersecurity company ClearSky published a report about the financially motivated CryptoCore campaign that targeted cryptocurrency wallets belonging to exchanges or their employees.

Hackers linked with the North Korean government applied the web skimming technique to steal cryptocurrency in a previously undocumented campaign that started early last year, researchers say. The attacks compromised customers of at least three online stores and relied on infrastructure used for web skimming activities and attributed in the past to Lazarus APT, also known as Hidden Cobra.

The North Korean-backed Lazarus hacking group used new malware with backdoor capabilities dubbed Vyveva n targeted attacks against a South African freight logistics company. Vyveva was first used in a June 2020 attack as ESET researchers discovered, but further evidence shows Lazarus has been deploying it in previous attacks going back to at least December 2018.

The same North Korean threat actors that targeted security researchers in January appear to be readying a new campaign using a fake company that aim to lure security professionals into another cyber-espionage trap. While researchers have seen no evidence yet of nefarious activity from attackers that leverage these web assets, it appears that attackers are gearing up to target security researchers again by the nature of the activity, according to Google TAG. Like previous websites that Google TAG has observed Zinc establish, the SecuriElite website has a link to the group's PGP public key at the bottom of the page, researchers noted.

A North Korean government-backed APT group has been caught using a fake pen-testing company and a range of sock puppet social media accounts in an escalation of a hacking campaign targeting security research professionals. The notorious hacking group, first exposed by Google earlier this year, returned on March 17th with a website for a fake penetration testing company.

Google's Threat Analysis Group says that North Korean government-sponsored hackers are once again targeting security researchers using fake Twitter and LinkedIn social media accounts. The hackers also created a website for a fake company named SecuriElite and supposedly offering offensive security services as the Google security team focused on hunting down state-backed hackers discovered on March 17.
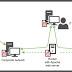
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry. The next-stage malware functions by embedding its malicious capabilities inside a Windows backdoor that offers features for initial reconnaissance and deploying malware for lateral movement and data exfiltration.