Security News
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021. "The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses Advanced Installer's Custom Actions feature to make the software installers execute the malicious scripts," Cisco Talos researcher Chetan Raghuprasad said in a technical report.

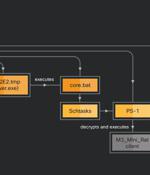
Json from CRED FILE NAMES file name array to GCLOUD CREDS FILES file name array[+] added netrc, kubeconfig, adc. Db from CRED FILE NAMES file name array[-] removed dload function[+] added commented dload function invocation for posting final results[+] added commented wget command to download and execute https://everlost.
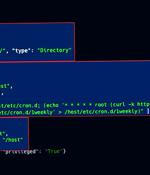
Exposed Kubernetes clusters are being exploited by malicious actors to deploy cryptocurrency miners and other backdoors. Cloud security firm Aqua, in a report shared with The Hacker News, said a majority of the clusters belonged to small to medium-sized organizations, with a smaller subset tied to bigger companies, spanning financial, aerospace, automotive, industrial, and security sectors.

Misconfigured and poorly secured Apache Tomcat servers are being targeted as part of a new campaign designed to deliver the Mirai botnet malware and cryptocurrency miners. The findings come...

A new fileless attack dubbed PyLoose has been observed striking cloud workloads with the goal of delivering a cryptocurrency miner, new findings from Wiz reveal. "The attack consists of Python code that loads an XMRig Miner directly into memory using memfd, a known Linux fileless technique," security researchers Avigayil Mechtinger, Oren Ofer, and Itamar Gilad said.

Internet-facing Linux systems and Internet of Things devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency. "The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations," Microsoft threat intelligence researcher Rotem Sde-Or said.

Ransomware actors and cryptocurrency scammers have joined nation-state actors in abusing cloud mining services to launder digital assets, new findings reveal. Earlier this March, Google Mandiant disclosed North Korea-based APT43's use of the hash rental and cloud mining services to obscure the forensic trail and wash the stolen cryptocurrency "Clean."

A financially motivated threat actor is actively scouring the internet for unprotected Apache NiFi instances to covertly install a cryptocurrency miner and facilitate lateral movement. "The attack script is not saved to the system. The attack scripts are kept in memory only."

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services Elastic Compute Cloud instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil.

Researchers have developed DarkBERT, a language model pretrained on dark web data, to help cybersecurity pros extract cyber threat intelligence from the Internet's virtual underbelly. A team of researchers from Korea Advanced Institute of Science and Technology and data intelligence company S2W has decided to test whether a custom-trained language model could be useful, so they came up with DarkBERT, which is pretrained on dark web data.