Security News

Security researchers are warning that threat actors could hijack Office 365 accounts to encrypt for a ransom the files stored in SharePoint and OneDrive services that companies use for cloud-based collaboration, document management and storage. A ransomware attack targeting files on these services could have severe consequences if backups aren't available, rendering important data inaccessible to owners and working groups.

Follina abuses Microsoft Office to execute remote code. CVE-2022-30190, also known as "Follina", is a remote code execution vulnerability that affects Microsoft Office, reported on May 27, 2022.

Microsoft Office apps - including Outlook and Teams - are vulnerable to homograph attacks based on internationalized domain names. "Users, who are trained to validate a link in an email client before they click it, will be susceptible to click on it because it has not yet been translated to a real domain name in their browser. The real domain name would only be seen after the page has started to open," Bitdefender researchers warned.

An advanced persistent threat actor aligned with Chinese state interests has been observed weaponizing the new zero-day flaw in Microsoft Office to achieve code execution on affected systems. "TA413 CN APT spotted exploiting the Follina zero-day using URLs to deliver ZIP archives which contain Word Documents that use the technique," enterprise security firm Proofpoint said in a tweet.

Infosec researchers have idenitied a zero-day code execution vulnerability in Microsoft's ubiquitous Office software. Dubbed "Follina", the vulnerability has been floating around for a while and uses Office functionality to retrieve a HTML file which in turn makes use of the Microsoft Support Diagnostic Tool to run some code.

A zero-day vulnerability in Microsoft Office allows adversaries to run malicious code on targeted systems via a flaw a remote Word template feature. Noted security researcher Kevin Beaumont dubbed the vulnerability "Follina", explaining the zero day code references the Italy-based area code of Follina - 0438.Beaumont said the flaw is abusing the remote template feature in Microsoft Word and is not dependent on a typical macro-based exploit path, common within Office-based attacks.

Security researchers have discovered a new Microsoft Office zero-day vulnerability that is being used in attacks to execute malicious PowerShell commands via Microsoft Diagnostic Tool simply by opening a Word document.The vulnerability, which has yet to receive a tracking number and is referred to by the infosec community as 'Follina,' is leveraged using malicious Word documents that execute PowerShell commands via the MSDT. This new Follina zero-day opens the door to a new critical attack vector leveraging Microsoft Office programs as it works without elevated privileges, bypasses Windows Defender detection, and does not need macro code to be enabled to execute binaries or scripts.
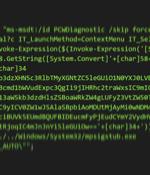
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. According to security researcher Kevin Beaumont, who dubbed the flaw "Follina," the maldoc leverages Word's remote template feature to fetch an HTML file from a server, which then makes use of the "Ms-msdt://" URI scheme to run the malicious payload. MSDT is short for Microsoft Support Diagnostics Tool, a utility that's used to troubleshoot and collect diagnostic data for analysis by support professionals to resolve a problem.

Microsoft is updating Microsoft Defender for Office 365 with differentiated protection for enterprise accounts tagged as critical for an organization. "We are introducing differentiated protection for Priority accounts, which will provide users tagged as Priority accounts with a higher level of protection," Microsoft explains on the Microsoft 365 roadmap.

Microsoft on Tuesday warned of an actively exploited zero-day flaw impacting Internet Explorer that's being used to hijack vulnerable Windows systems by leveraging weaponized Office documents. "Microsoft is investigating reports of a remote code execution vulnerability in MSHTML that affects Microsoft Windows. Microsoft is aware of targeted attacks that attempt to exploit this vulnerability by using specially-crafted Microsoft Office documents," the company said.