Security News
The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers...

Today, Google announced new security features coming to Android 15 and Google Play Protect that will help block scams, fraud, and malware apps on users' devices. "Today, we're announcing more new fraud and scam protection features coming in Android 15 and Google Play services updates later this year to help better protect users around the world," reads a Google blog post from Dave Kleidermacher, VP Engineering, Android Security and Privacy.

Today, Google announced new security features coming to Android 15 and Google Play that will help block scams, fraud, and malware apps on users' devices. "Today, we're announcing more new fraud and scam protection features coming in Android 15 and Google Play services updates later this year to help better protect users around the world," reads a Google blog post from Dave Kleidermacher, VP Engineering, Android Security and Privacy.

Threat actors are taking advantage of the flawed design of Foxit PDF Reader's alerts to deliver malware via booby-trapped PDF documents, Check Point researchers have warned. The researchers have analyzed several campaigns using malicious PDF files that are targeting Foxit Reader users.
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from...

Microsoft has fixed a zero-day vulnerability exploited in attacks to deliver QakBot and other malware payloads on vulnerable Windows systems. Kaspersky security researchers discovered the vulnerability while investigating another Windows DWM Core Library privilege escalation bug tracked as CVE-2023-36033 and also exploited as a zero-day in attacks.

A malware botnet known as 'Ebury' has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023. "While 400,000 is a massive number, it's important to mention that this is the number of compromises over the course of almost 15 years. Not all of those machines were compromised at the same time," explains ESET. "There is a constant churn of new servers being compromised while others are being cleaned up or decommissioned. The data at our disposal doesn't indicate when the attackers lost access to the systems, so it's difficult to know the size of the botnet at any specific point in time."
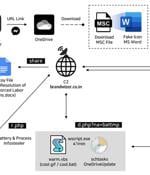
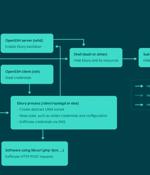
The North Korean threat actor tracked as Kimsuky has been observed deploying a previously undocumented Golang-based malware dubbed Durian as part of highly-targeted cyber attacks aimed at South...

Polish government institutions have been targeted as part of a large-scale malware campaign orchestrated by a Russia-linked nation-state actor called APT28. "The campaign sent emails with content...

A newer version of a malware loader called Hijack Loader has been observed incorporating an updated set of anti-analysis techniques to fly under the radar. "These enhancements aim to increase the...