Security News
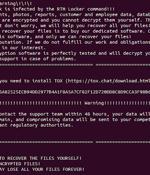
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system. "Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday.

The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033. Alloy Taurus is the constellation-themed moniker assigned to a threat actor that's known for its attacks targeting telecom companies since at least 2012.

Hackers are deploying new Linux malware variants in cyberespionage attacks, such as a new PingPull variant and a previously undocumented backdoor tracked as 'Sword2033. PingPull is a RAT first documented by Unit 42 last summer in espionage attacks conducted by the Chinese state-sponsored group Gallium, also known as Alloy Taurus.

A new Lazarus campaign considered part of "Operation DreamJob" has been discovered targeting Linux users with malware for the first time. Lazarus' Operation DreamJob, also known as Nukesped, is an ongoing operation targeting people who work in software or DeFi platforms with fake job offers on LinkedIn or other social media and communication platforms.

The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users. The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.

The Pakistan-based advanced persistent threat actor known as Transparent Tribe used a two-factor authentication tool used by Indian government agencies as a ruse to deliver a new Linux backdoor called Poseidon. Transparent Tribe is also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, and has a track record of targeting Indian government organizations, military personnel, defense contractors, and educational entities.

"The kernel failed to protect applications that attempted to protect against Spectre v2, leaving them open to attack from other processes running on the same physical core in another hyperthread," the vulnerability disclosure explains. Linux kernel 6.0 debuts, Linus Torvalds teases 'core new things' coming in version 6.1 Older AMD, Intel chips vulnerable to data-leaking 'Retbleed' Spectre variant Apple gets lawsuit over Meltdown and Spectre dismissed Boffins release tool to decrypt Intel microcode.

A Chinese state-sponsored threat activity group tracked as RedGolf has been attributed to the use of a custom Windows and Linux backdoor called KEYPLUG. "RedGolf is a particularly prolific Chinese state-sponsored threat actor group that has likely been active for many years against a wide range of industries globally," Recorded Future told The Hacker News. The use of KEYPLUG by Chinese threat actors was first disclosed by Google-owned Manidant in March 2022 in attacks targeting multiple U.S. state government networks between May 2021 and February 2022.

A group of academics from Northeastern University and KU Leuven has disclosed a fundamental design flaw in the IEEE 802.11 Wi-Fi protocol standard, impacting a wide range of devices running Linux, FreeBSD, Android, and iOS. Successful exploitation of the shortcoming could be abused to hijack TCP connections or intercept client and web traffic, researchers Domien Schepers, Aanjhan Ranganathan, and Mathy Vanhoef said in a paper published this week. Besides manipulating the security context to leak frames from the queue, an attacker can override the client's security context used by an access point to receive packets intended for the victim.

Taiwanese hardware vendor QNAP warns customers to secure their Linux-powered network-attached storage devices against a high-severity Sudo privilege escalation vulnerability. The vulnerability also affects the QTS, QuTS hero, QuTScloud, and QVP NAS operating systems, as QNAP revealed in a security advisory published on Wednesday.