Security News

Apple recently addressed a macOS vulnerability that allows attackers to bypass System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions. [...]

CISA has warned U.S. federal agencies to secure their systems against ongoing attacks targeting a high-severity Windows kernel vulnerability. [...]

Cybersecurity researchers have shed light on what has been described as the first Unified Extensible Firmware Interface (UEFI) bootkit designed for Linux systems. Dubbed Bootkitty by its creators...

Microsoft has announced the Windows Resiliency Initiative, aimed at avoiding a repeat of the prolonged worldwide IT outage caused by a buggy CrowdStrike update that took down millions of Windows...

OpenPaX is an open-source kernel patch that mitigates common memory safety errors, re-hardening systems against application-level memory safety attacks using a simple Linux kernel patch. It’s...

A new attack technique could be used to bypass Microsoft's Driver Signature Enforcement (DSE) on fully patched Windows systems, leading to operating system (OS) downgrade attacks. "This bypass...

Attackers can downgrade Windows kernel components to bypass security features such as Driver Signature Enforcement and deploy rootkits on fully patched systems. [...]
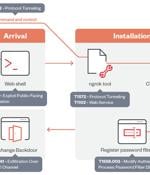
The Iranian threat actor known as OilRig has been observed exploiting a now-patched privilege escalation flaw impacting the Windows Kernel as part of a cyber espionage campaign targeting the...

Cybersecurity researchers have shed light on a novel Linux kernel exploitation technique dubbed SLUBStick that could be exploited to elevate a limited heap vulnerability to an arbitrary memory...
Google released 46 fixes for Android in its August security patch batch, including one for a Linux kernel flaw in the mobile OS that can lead to remote code execution. While Google never provides much detail in its monthly patch bulletins about how Android flaws are being abused in the wild, it does note that "There are indications that CVE-2024-36971 may be under limited, targeted exploitation."