Security News

The Iranian APT has been exploiting Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021, according to the alert. In keeping with what CISA described on Wednesday, MSTIC has seen the Iran-linked Phosphorous group - aka a number of names, including Charming Kitten, TA453, APT35, Ajax Security Team, NewsBeef and Newscaster - globally target the Exchange and Fortinet flaws "With the intent of deploying ransomware on vulnerable networks."

"FBI and CISA have observed this Iranian government-sponsored APT group exploit Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021 to gain initial access to systems in advance of follow-on operations, which include deploying ransomware," CISA said. The Iranian state hackers focus their attacks on US critical infrastructure sectors and Australian organizations.

The Microsoft Threat Intelligence Center has presented an analysis of the evolution of several Iranian threat actors at the CyberWarCon 2021, and their findings show increasingly sophisticated attacks. Since September 2020, Microsoft has been tracking six Iranian hacking groups deploying ransomware and exfiltrating data to cause disruption and destruction for victims.

The Federal Bureau of Investigation warned private industry partners of attempts by an Iranian threat actor to buy stolen information regarding US and worldwide organizations. According to the FBI, the threat actor will likely use the leaked data bought from clear and dark web sources to breach the systems of related organizations.

The Iranian state-supported APT known as 'Lyceum' targeted ISPs and telecommunication service providers in the Middle East and Africa between July and October 2021. Apart from Israel, which is permanently in the crosshairs of Iranian hackers, researchers have spotted Lyceum backdoor malware attacks in Morocco, Tunisia, and Saudi Arabia.

An attack on the fuel distribution chain in Iran reportedly forced the shutdown of a network of filling stations Tuesday, leaving motorists stranded at pumps across the country and unable to fill up their tanks. The incident disabled government-issued electronic cards providing subsidies that many Iranians use to purchase fuel at discounted prices, according to a report in The Times of Israel, which said that the Iran Supreme National Security Council confirmed the attack.

An attack on the fuel distribution chain in Iran reportedly forced the shutdown of a network of filling stations Tuesday, leaving motorists stranded at pumps across the country and unable to fill up their tanks. The incident disabled government-issued electronic cards providing subsidies that many Iranians use to purchase fuel at discounted prices, according to a report in The Times of Israel, which said that the Iran Supreme National Security Council confirmed the attack.

Gas stations from the National Iranian Oil Products Distribution Company have stopped working today due to a cyberattack that affected the entire distribution network. The NIOPDC network has more than 3,500 stations across the country and has been supplying oil products for more than 80 years.
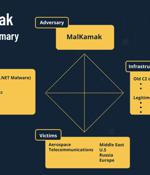
Details have emerged about a new cyber espionage campaign directed against the aerospace and telecommunications industries, primarily in the Middle East, with the goal of stealing sensitive information about critical assets, organizations' infrastructure, and technology while remaining in the dark and successfully evading security solutions. "The ShellClient RAT has been under ongoing development since at least 2018, with several iterations that introduced new functionalities, while it evaded antivirus tools and managed to remain undetected and publicly unknown," researchers Tom Fakterman, Daniel Frank, Chen Erlich, and Assaf Dahan said in a technical deep dive published today.

IT and communication companies in Israel were at the center of a supply chain attack campaign spearheaded by an Iranian threat actor that involved impersonating the firms and their HR personnel to target victims with fake job offers in an attempt to penetrate their computers and gain access to the company's clients. ClearSky theorized that the attacks' focus on IT and communication companies suggest they are intended to facilitate supply chain attacks on their clients.