Security News

U.S. cybersecurity and intelligence agencies have warned of Phobos ransomware attacks targeting government and critical infrastructure entities, outlining the various tactics and techniques the...

In a speech delivered yesterday, Mike Burgess noted that countering Soviet sabotage plots was a significant reason ASIO was created. "Nationalists and racists are probably just mouthing off. But the spy chief indicated that ASIO"is aware of one nation-state conducting multiple attempts to scan critical infrastructure in Australia and other countries, targeting water, transport and energy networks.

NIST has expanded the CSF's core guidance and developed related resources to help users get the most out of the framework."The NIST CSF 2.0 update significantly impacts the security of software supply chains, addressing the integration of open source, commercial components, in-house developed software, and Commercial Off-The-Shelf products. NIST CSF 2.0 could be a key instrument for helping CISOs better define and build up controls that will improve security outcomes, providing direction to address critical asset protection, reduce or eliminate risk of material impact, and prevent any breach of duty for failing to adhere to regulatory and compliance regulations," Saša Zdjelar, Chief Trust Officer at ReversingLabs, told Help Net Security.

Over 29% of IT leaders found that moving projects from on-premises to the cloud was more expensive than expected, while 65% said it was financially predictable. The cost-benefit analysis of cloud versus on-premises infrastructure varies greatly depending on the organization.

PSI Software SE, a German software developer for complex production and logistics processes, has confirmed that the cyber incident it disclosed last week is a ransomware attack that impacted its internal infrastructure. The company operates at a global level with a staff of more than 2,000 and specializes in software solutions for major energy suppliers.

In the wake of yesterday's surprise law enforcement takeover of LockBit's leak site, the UK National Crime Agency and Europol have shared more information about the extent of the takedown. "Today, after infiltrating the group's network, the NCA has taken control of the infrastructure that allows the Lockbit service to operate, compromising their entire criminal enterprise and damaging their credibility," the Agency said.

Threat actors are leveraging a recently disclosed security flaw impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy a backdoor codenamed DSLog on susceptible devices. That's...

The FBI dismantled the Warzone RAT malware operation, seizing infrastructure and arresting two individuals associated with the cybercrime operation. Warzone RAT is commodity malware created in 2018 that offers numerous features to aid cybercrime, including UAC bypass, hidden remote desktop, cookie and password stealing, keylogging, webcam recording, file operations, reverse proxy, remote shell, and process management.
The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used to sell a remote access trojan (RAT) called Warzone RAT. The domains – www.warzone[.]ws and...
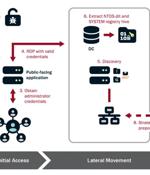
The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five...