Security News

In an effort to grow its hybrid cloud and artificial intelligence capabilities, IBM announced on Tuesday that it was acquiring Polar Security, an Israel-based company specializing in data security posture management. A 2023 study by Gartner, looking at DSPM functions and capabilities, reported that DSPM solutions are getting savvier at uncovering data repositories and identifying their exposure risk, thanks to their ability to use data lineage to "Discover, identify and map data, across structured and unstructured data repositories, that relies on integrations with, for example, specific infrastructure, databases and CSPs.".

At the RSA Conference, IBM launched a platform-centric expansion to its QRadar security product, designed as a one-stop shop to accelerate response and offer a unified framework for security operations centers. "Today's Security Operation Center teams are protecting a fast-expanding digital footprint that extends across hybrid cloud environments - creating complexity and making it hard to keep pace with accelerating attack speeds," according to IBM, which also said the products are specifically meant to help buttress security operations center teams facing labor-intensive alert investigations and response processes, manual analysis and the proliferation of tools, data, points of engagement, APIs and other potential vulnerabilities.
Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors in hacks targeting unpatched systems. CVE-2022-46169 relates to a critical authentication bypass and command injection flaw in Cacti servers that allows an unauthenticated user to execute arbitrary code.

Attackers are exploiting a critical vulnerability in the IBM Aspera Faspex centralized file transfer solution to breach organizations. IBM Aspera Faspex is used by organizations to allow employees to quickly and securely exchange files with each other.

A previously known Windows-based ransomware strain known as IceFire has expanded its focus to target Linux enterprise networks belonging to several media and entertainment sector organizations across the world. The intrusions entail the exploitation of a recently disclosed deserialization vulnerability in IBM Aspera Faspex file-sharing software, according to cybersecurity company SentinelOne.

The IBM report noted that ransomware declined 4 percentage points between 2021 and 2022, and defenders were more successful at detecting and preventing those attacks. Cyberattackers have gotten much faster at infiltrating perimeters, with the average time to complete a ransomware attack dropping from two months to less than four days.
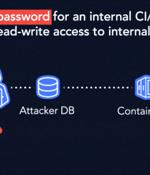
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."
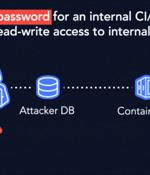
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."

IBM has started offering quantum-resistant crypto - using the quantum-resistant crypto recommended by the US National Institute of Standards and Technology. China is felt to be stealing data today, safe in the knowledge its future quantum computers will be able to decrypt it in the near future.

IBM has expanded its extensive cybersecurity portfolio by acquiring Randori - a four-year-old startup that specializes in helping enterprises manage their attack surface by identifying and prioritizing their external-facing on-premises and cloud assets. Its plan is to give the computing behemoth's customers a tool to manage their security posture by looking at their infrastructure from a threat actor's point-of-view - a position IBM hopes will allow users to identify unseen weaknesses.