Security News

A U.K. citizen who took part in the massive July 2020 hack of Twitter has been sentenced to five years in prison in the U.S. Joseph James O'Connor, 24, was awarded the sentence on Friday in the Southern District of New York, a little over a month after he pleaded guilty to the criminal schemes. The infamous Twitter breach allowed the defendant and his co-conspirators to obtain unauthorized access to backend tools used by Twitter, abusing them to hijack 130 popular accounts to perpetrate a crypto scam that netted them about $120,000 in illegal profits.

Three of them were exploited by Russian APT28 cyberspies to hack into Roundcube email servers belonging to Ukrainian government organizations. While the KEV catalog's primary focus is alerting federal agencies of exploited vulnerabilities that must be patched as soon as possible, it is also highly advised that private companies worldwide prioritize addressing these bugs.

Microsoft says Internet-exposed Linux and Internet of Things devices are being hijacked in brute-force attacks as part of a recently observed cryptojacking campaign. After gaining access to a system, the attackers deploy a trojanized OpenSSH package that helps them backdoor the compromised devices and steal SSH credentials to maintain persistence.
The Chinese cyber espionage actor known as Camaro Dragon has been observed leveraging a new strain of self-propagating malware that spreads through compromised USB drives. The cybersecurity company, which found evidence of USB malware infections in Myanmar, South Korea, Great Britain, India, and Russia, said the findings are the result of a cyber incident that it investigated at an unnamed European hospital in early 2023.

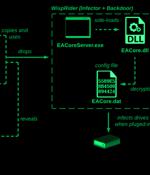
The North Korean APT37 hacking group uses a new 'FadeStealer' information-stealing malware containing a 'wiretapping' feature, allowing the threat actor to snoop and record from victims' microphones. In a new report from the AhnLab Security Emergency Response Center, researchers provide information on new custom malware dubbed 'AblyGo backdoor' and 'FadeStealer' that the threat actors use in cyber espionage attacks.

The North Korean threat actor known as ScarCruft has been observed using an information-stealing malware with previous undocumented wiretapping features as well as a backdoor developed using Golang that exploits the Ably real-time messaging service. "The threat actor sent their commands through the Golang backdoor that is using the Ably service," the AhnLab Security Emergency response Center said in a technical report.

Foreign affairs ministries in the Americas have been targeted by a Chinese state-sponsored actor named Flea as part of a recent campaign that spanned from late 2022 to early 2023. The cyber attacks, per Broadcom's Symantec, involved a new backdoor codenamed Graphican.

The Chinese state-sponsored hacking group tracked as APT15 has been observed using a novel backdoor named 'Graphican' in a new campaign between late 2022 and early 2023. APT15, also known as Nickel, Flea, Ke3Chang, and Vixen Panda, are Chinese state hackers targeting important public and private organizations worldwide since at least 2004.

VMware has flagged that a recently patched critical command injection vulnerability in Aria Operations for Networks has come under active exploitation in the wild. The flaw, tracked as CVE-2023-20887, could allow a malicious actor with network access to the product to perform a command injection attack, resulting in remote code execution.

The ransomware operation behind a cyberattack on the University of Manchester has begun to email students, warning that their data will soon be leaked after an extortion demand was not paid. The threat actors claim to have stolen 7 TB of data from the University of Manchester during a June 6th cyberattack in an email sent to students and shared with BleepingComputer.