Security News

Hackers are using a fake Android app named 'SafeChat' to infect devices with spyware malware that steals call logs, texts, and GPS locations from phones. The Android spyware is suspected to be a variant of "Coverlm," which steals data from communication apps such as Telegram, Signal, WhatsApp, Viber, and Facebook Messenger.

Hackers are actively exploiting a 'BleedingPipe' remote code execution vulnerability in Minecraft mods to run malicious commands on servers and clients, allowing them to take control of the devices. BleedingPipe is a vulnerability found in many Minecraft mods caused by the incorrect use of deserialization in the 'ObjectInputStream' class in Java to exchange network packets between servers and clients.

Threat actors associated with the hacking crew known as Patchwork have been spotted targeting universities and research organizations in China as part of a recently observed campaign. "Patchwork relied on a range of elaborate fictitious personas to socially engineer people into clicking on malicious links and downloading malicious apps," the social media giant said.
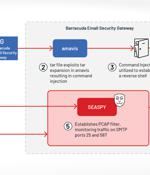
The U.S. Cybersecurity and Infrastructure Security Agency on Friday disclosed details of a "Novel persistent backdoor" called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway appliances. The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868, which allows for remote command injection.
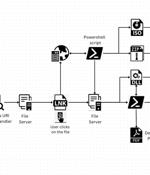
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT. The novel attack technique, per Trellix, takes advantage of the "Search-ms:" URI protocol handler, which offers the ability for applications and HTML links to launch custom local searches on a device, and the "Search:" application protocol, a mechanism for calling the desktop search application on Windows. It's worth noting that clicking on the link also generates a warning "Open Windows Explorer?," approving which "The search results of remotely hosted malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results," the researchers explained.

CoinsPaid is blaming the attack on the North Korean hacking group Lazarus, saying that the sophisticated financially-motivated state-backed actor was aiming for a higher cash-out. "We believe Lazarus expected the attack on CoinsPaid to be much more successful," reads the CoinsPaid press release.

While consumers are usually the ones worried about their information being exposed in data breaches, it's now the hacker's turn, as the notorious Breached cybercrime forum's database is up for sale and member data shared with Have I Been Pwned. Yesterday, the Have I Been Pwned data breach notification service announced that visitors can check if their information was exposed in a data breach of the Breached cybercrime forum.

Popular WordPress form-building plugin Ninja Forms contains three vulnerabilities that could allow attackers to achieve privilege escalation and steal user data. The second and third problems, tracked as CVE-2023-38393 and CVE-2023-38386, respectively, are broken access control issues on the plugin's form submissions export feature, allowing Subscribers and Contributors to export all of the data that users have submitted on the impacted WordPress site.

Misconfigured and poorly secured Apache Tomcat servers are being targeted as part of a new campaign designed to deliver the Mirai botnet malware and cryptocurrency miners. The findings come...

Blockchain analysts blame the North Korean Lazarus hacking group for a recent attack on payment processing platform Alphapo where the attackers stole almost $60 million in crypto. [...]