Security News

The number of Cisco IOS XE devices detected with a malicious backdoor implant has plummeted from over 50,000 impacted devices to only a few hundred after the attackers updated the backdoor to hide infected systems from scans. This week, Cisco warned that hackers exploited two zero-day vulnerabilities, CVE-2023-20198 and CVE-2023-20273, to hack over 50,000 Cisco IOS XE devices to create privileged user accounts and install a malicious LUA backdoor implant.

A new sophisticated threat tracked as 'TetrisPhantom' has been using compromised secure USB drives to target government systems in the Asia-Pacific region. Secure USB drives store files in an encrypted part of the device and are used to safely transfer data between systems, including those in an air-gapped environment.
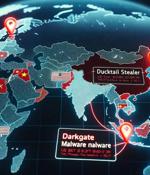
Attacks leveraging the DarkGate commodity malware targeting entities in the U.K., the U.S., and India have been linked to Vietnamese actors associated with the use of the infamous Ducktail...

State-sponsored North Korean hackers have significantly intensified their focus on the IT sector in recent years, by infiltrating firms developing software and companies lookind for IT workers. "In past operations, Diamond Sleet and other North Korean threat actors have successfully carried out software supply chain attacks by infiltrating build environments," Microsoft noted.

The Iranian hacking group tracked as MuddyWater breached at least twelve computers belonging to a Middle Eastern government network and maintained access for eight months between February and September 2023. The attacks observed by Symantec began on February 1, 2023, and utilize a wide assortment of malware, tools, and malicious activity that lasted for 8 months.

Microsoft says that the North Korean Lazarus and Andariel hacking groups are exploiting the CVE-2023-42793 flaw in TeamCity servers to deploy backdoor malware, likely to conduct software supply chain attacks. In September, TeamCity fixed a critical 9.8/10 vulnerability tracked as CVE-2023-42793 that allowed unauthenticated attackers to remotely execute code.

A hacker has leaked an additional 4.1 million stolen 23andMe genetic data profiles for people in Great Britain and Germany on a hacking forum.23andMe told BleepingComputer that this data was obtained through credential stuffing attacks on accounts using weak passwords or credentials exposed in other data breaches.

Google's Threat Analysis Group, a team of security experts who defend Google users from state-sponsored attacks, has detected state hackers from several countries targeting the bug, including the Sandworm, APT28, and APT40 threat groups from Russia and China. In an early September attack, Russian Sandworm hackers delivered Rhadamanthys infostealer malware in phishing attacks using fake invitations to join a Ukrainian drone training school.
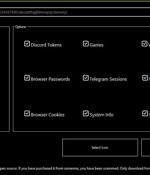
In what's the latest evolution of threat actors abusing legitimate infrastructure for nefarious ends, new findings show that nation-state hacking groups have entered the fray in leveraging the...

A critical severity vulnerability impacting Royal Elementor Addons and Templates up to version 1.3.78 is reported to be actively exploited by two WordPress security teams. Two WordPress security firms, Wordfence and WPScan, have marked CVE-2023-5360 as actively exploited since August 30, 2023, with the attack volume ramping up starting on October 3, 2023.