Security News

Microsoft says North Korean hacking groups have breached multiple Russian government and defense targets since the start of the year. "Multiple North Korean threat actors have recently targeted the Russian government and defense industry - likely for intelligence collection - while simultaneously providing material support for Russia in its war on Ukraine," said Clint Watts, the head of Microsoft's Digital Threat Analysis Center.

Google's Threat Analysis Group says North Korean state hackers are again targeting security researchers in attacks using at least one zero-day in an undisclosed popular software. Researchers attacked in this campaign are involved in vulnerability research and development, according to Google's team of security experts that protects the company's users from state-sponsored attacks.

The mystery of how Chinese hackers managed to steal a crucial signing key that allowed them to breach Microsoft 365's email service and access accounts of employees of 25 government agencies has been explained: they found it somewhere where it shouldn't have been - Microsoft's corporate environment. The signing key was included in the snapshot of the crashed process of a consumer signing system because of an unexpected race condition, and its presence in the crash dump wasn't detected by Microsoft's credential scanning methods.

Data you don't control is open to causing you harm. The fact that nearly everyone in the US apparently likes "Instant gratification convenience over their long term security" suggests they have not yet had a piece ripped out of them.

Microsoft says Storm-0558 Chinese hackers stole a signing key used to breach government email accounts from a Windows crash dump after compromising a Microsoft engineer's corporate account. While investigating Storm-0558's attack, Microsoft found that the MSA key was leaked into a crash dump after a consumer signing system crashed in April 2021.

Online cryptocurrency casino Stake.com announced that its ETH/BSC hot wallets had been compromised to perform unauthorized transactions, with over $40 million in crypto reportedly stolen. The threat group was linked to the theft of $35 million from Atomic Wallet in June, $60 million from Alphapo in July, and another $37.3 million from CoinsPaid also in July.

Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary code, and potentially take over servers. MinIO is an open-source object storage service offering compatibility with Amazon S3 and the ability to store unstructured data, logs, backups, and container images of up to 50TB in size.

The attackers' goal was to hijack highly-privileged Okta Super Administrator accounts to access and abuse identity federation features that allowed impersonating users from the compromised organization. After a successful compromise of a Super Admin account, the threat actor used anonymizing proxy services, a fresh IP address, and a new device.
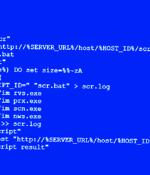
An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance object storage system to achieve unauthorized code execution on affected servers. Cybersecurity and incident response firm Security Joes said the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.

Forever 21 clothing and accessories retailer is sending data breach notifications to more than half a million individuals who had their personal information exposed to network intruders.The investigation revealed that hackers had intermittent access to Forever 21 systems between January and March this year and leveraged this access to steal data.