Security News

Malicious activity targeting a critical severity flaw in the 'Better Search Replace' WordPress plugin has been detected, with researchers observing thousands of attempts in the past 24 hours. Better Search Replace is a WordPress plugin with more than one million installations that helps with search and replace operations in databases when moving websites to new domains or servers.

Cozy Bear has been busy hacking and spying on big tech companies: both Microsoft and Hewlett Packard Enterprise have recently disclosed successful attack campaigns by the Russia-affiliated APT group. Last Friday, Microsoft revealed that a threat-actor identified as Midnight Blizzard - a hacking group believed to be associated with the Russian Foreign Intelligence Service - has breached their corporate systems on January 12, 2024.
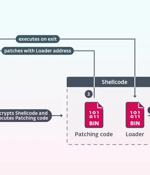
A previously undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that hijack update requests from legitimate software to deliver a...

Hackers with links to the Kremlin are suspected to have infiltrated information technology company Hewlett Packard Enterprise's (HPE) cloud email environment to exfiltrate mailbox data. "The...

Hewlett Packard Enterprise disclosed today that suspected Russian hackers known as Midnight Blizzard gained access to the company's Microsoft Office 365 email environment to steal data from its cybersecurity team and other departments. In a new Form 8-K SEC filing, HPE says they were notified on December 12th that the suspected Russian hackers breached their cloud-based email environment in May 2023.

Governments from Australia, the U.K., and the U.S. have imposed financial sanctions on a Russian national for his alleged role in the 2022 ransomware attack against health insurance provider...

The Australian, US, and UK governments have announced sanctions for Aleksandr Gennadievich Ermakov, a Russian national considered responsible for the 2022 Medibank hack and a member of the REvil ransomware group. Medibank is a large health insurance provider in Australia that suffered a ransomware attack in October 2022, causing operational and business disruption.

The Australian government has announced sanctions for Aleksandr Gennadievich Ermakov, a Russian national considered responsible for the 2022 Medibank hack and a member of the REvil ransomware group. Following a lengthy investigation, the Australian authorities identified Ermakov as the person responsible for the Medibank hack and data theft.

Media organizations and high-profile experts in North Korean affairs have been at the receiving end of a new campaign orchestrated by a threat actor known as ScarCruft in December 2023. "ScarCruft...

Several public and popular libraries abandoned but still used in Java and Android applications have been found susceptible to a new software supply chain attack method called MavenGate. "Access to...