Security News

Nation-state actors associated with Russia, North Korea, Iran, and China are experimenting with artificial intelligence (AI) and large language models (LLMs) to complement their ongoing cyber...

Microsoft has patched today a Windows Defender SmartScreen zero-day exploited in the wild by a financially motivated threat group to deploy the DarkMe remote access trojan.The hacking group was spotted using the zero-day in attacks on New Year's Eve day by Trend Micro security researchers.

The paperback version of A Hacker's Mind has just been published. This is the real reason I am posting this-Amazon has significantly discounted the hardcover to $15 to get rid of its stock.

Hackers are believed to have used a stolen private key to mint and steal over 1.79 billion PLA tokens, a cryptocurrency used within the PlayDapp ecosystem. PlayDapp is a blockchain-based platform that uses and trades non-fungible tokens within games, allowing users to buy, sell, and trade digital assets across various games without intermediaries.

Hackers are believed to have used a stolen private key to mint and steal over $290 million in PLA tokens, a cryptocurrency used within the PlayDapp ecosystem. PlayDapp is a blockchain-based platform that uses and trades non-fungible tokens within games, allowing users to buy, sell, and trade digital assets across various games without intermediaries.

Hackers are exploiting a server-side request forgery vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy the new DSLog backdoor on vulnerable devices. The flaw impacts the SAML component of the mentioned products and allows attackers to bypass authentication and access restricted resources on Ivanti gateways running versions 9.x and 22.x. The updates that fix the problem are Ivanti Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Ivanti Policy Secure version 22.5R1.1, and ZTA version 22.6R1.3.

When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential...
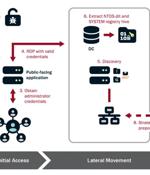
The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five...

The Chinese Volt Typhoon cyber-espionage group infiltrated a critical infrastructure network in the United States and remained undetected for at least five years before being discovered, according to a joint advisory from CISA, the NSA, the FBI, and partner Five Eyes agencies. Volt Typhoon hackers are known for extensively using living off the land techniques as part of their attacks on critical infrastructure organizations.

Chinese Volt Typhoon state hackers failed to revive a botnet recently taken down by the FBI, which was previously used in attacks targeting critical infrastructure across the United States. After obtaining a court order authorizing it to dismantle the botnet on December 6, FBI agents took control of one of its command-and-control servers and cut off the Chinese hackers' access to the infected devices.