Security News

The U.S. Department of Justice (DoJ) on Thursday announced charges against a 36-year-old Yemeni national for allegedly deploying the Black Kingdom ransomware against global targets, including...

A California man who used the alias "NullBulge" has pleaded guilty to illegally accessing Disney's internal Slack channels and stealing over 1.1 terabytes of internal company data. [...]

Enterprise data backup platform Commvault has revealed that an unknown nation-state threat actor breached its Microsoft Azure environment by exploiting CVE-2025-3928 but emphasized there is no...

A China-aligned APT threat actor named "TheWizards" abuses an IPv6 networking feature to launch adversary-in-the-middle (AitM) attacks that hijack software updates to install Windows malware. [...]
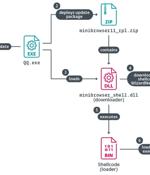
A China-aligned advanced persistent threat (APT) group called TheWizards has been linked to a lateral movement tool called Spellbinder that can facilitate adversary-in-the-middle (AitM) attacks....

Threat actors are intensifying internet-wide scanning for Git configuration files that can reveal sensitive secrets and authentication tokens used to compromise cloud services and source code...

Today, the French foreign ministry blamed the APT28 hacking group linked to Russia's military intelligence service (GRU) for targeting or breaching a dozen French entities over the last four years. [...]

Threat actors have been observed exploiting two newly disclosed critical security flaws in Craft CMS in zero-day attacks to breach servers and gain unauthorized access. The attacks, first observed...
North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute malware during the fake hiring process. "In this new campaign, the threat actor...

The FBI has asked the public for information on Chinese Salt Typhoon hackers behind widespread breaches of telecommunications providers in the United States and worldwide. [...]