Security News

T-Mobile says the Chinese "Salt Typhoon" hackers who recently compromised its systems as part of a series of telecom breaches first hacked into some of its routers to explore ways to navigate...
The threat actor known as APT-C-60 has been linked to a cyber attack targeting an unnamed organization in Japan that used a job application-themed lure to deliver the SpyGlace backdoor. That's...

America's Cyber Defense Agency has received evidence of hackers actively exploiting a remote code execution vulnerability in SSL VPN products Array Networks AG and vxAG ArrayOS. [...]


The China-linked threat actor known as Earth Estries has been observed using a previously undocumented backdoor called GHOSTSPIDER as part of its attacks targeting Southeast Asian...

Russia-aligned APT group RomCom was behind attacks that leveraged CVE-2024-9680, a remote code execution flaw in Firefox, and CVE-2024-49039, an elevation of privilege vulnerability in Windows...

Forest Blizzard, a threat group associated with Russia’s GRU military intelligence service, repeatedly breached a US-based organization via compromised computer systems of nearby firms, which they...

The Chinese state-sponsored hacking group Salt Typhoon has been observed utilizing a new "GhostSpider" backdoor in attacks against telecommunication service providers. [...]

Six sites targeted for security clean-up, just 49,994 to go A plan for hackers to help secure America's critical infrastructure has kicked off with six US water companies signing up to let coders...

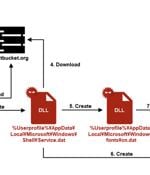
A new malicious campaign is using a legitimate but old and vulnerable Avast Anti-Rootkit driver to evade detection and take control of the target system by disabling security components. [...]