Security News

A suspected ransomware intrusion against an unnamed target leveraged a Mitel VoIP appliance as an entry point to achieve remote code execution and gain initial access to the environment.The findings come from cybersecurity firm CrowdStrike, which traced the source of the attack to a Linux-based Mitel VoIP device sitting on the network perimeter, while also identifying a previously unknown exploit as well as a couple of anti-forensic measures adopted by the actor on the device to erase traces of their actions.

A China-based advanced persistent threat group is possibly deploying short-lived ransomware families as a decoy to cover up the true operational and tactical objectives behind its campaigns. The activity cluster, attributed to a hacking group dubbed Bronze Starlight by Secureworks, involves the deployment of post-intrusion ransomware such as LockFile, Atom Silo, Rook, Night Sky, Pandora, and LockBit 2.0.

Hackers used a zero-day exploit on Linux-based Mitel MiVoice VOIP appliances for initial access in what is believed to be the beginning of a ransomware attack. Mitel VOIP devices are used by critical organizations in various sectors for telephony services and were recently exploited by threat actors for high-volume DDoS amplification attacks.
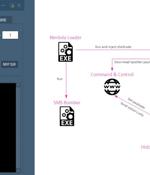
The novel loader, dubbed Nimbda, is "Bundled with a Chinese language greyware 'SMS Bomber' tool that is most likely illegally distributed in the Chinese-speaking web," Israeli cybersecurity company Check Point said in a report. "Whoever crafted the Nim loader took special care to give it the same executable icon as the SMS Bomber that it drops and executes," the researchers said.

Two Chinese hacking groups conducting cyber espionage and stealing intellectual property from Japanese and western companies are deploying ransomware as a decoy to cover up their malicious activities. Threat analysts from Secureworks say that the use of ransomware in espionage operations is done to obscure their tracks, make attribution harder, and create a powerful distraction for defenders.

An advanced persistent threat actor codenamed ToddyCat has been linked to a string of attacks aimed at high-profile entities in Europe and Asia since at least December 2020. The relatively new adversarial collective is said to have commenced its operations by targeting Microsoft Exchange servers in Taiwan and Vietnam using an unknown exploit to deploy the China Chopper web shell and activate a multi-stage infection chain.

The Computer Emergency Response Team of Ukraine has cautioned of a new set of spear-phishing attacks exploiting the "Follina" flaw in the Windows operating system to deploy password-stealing malware. Attributing the intrusions to a Russian nation-state group tracked as APT28, the agency said the attacks commence with a lure document titled "Nuclear Terrorism A Very Real Threat.rtf" that, when opened, exploits the recently disclosed vulnerability to download and execute a malware called CredoMap.

Cybersecurity researchers have discovered a new campaign attributed to the Chinese "Tropic Trooper" hacking group, which employs a novel loader called Nimbda and a new variant of the Yahoyah trojan. The trojan is bundled in a greyware tool named 'SMS Bomber,' which is used for denial of service attacks against phones, flooding them with messages.

The Ukrainian Computer Emergency Response Team is warning that Russian hacking groups are exploiting the Follina code execution vulnerability in new phishing campaigns to install the CredoMap malware and Cobalt Strike beacons. The RTF document used in the APT28 campaign attempts to exploit CVE-2022-30190, aka "Follina," to download and launch the CredoMap malware on a target's device.

Capital One Financial Corporation announced [] that on July 19, 2019, it determined there was unauthorized access by an outside individual who obtained certain types of personal information relating to people who had applied for its credit card products and to Capital One credit card customers. As you will notice from the OCC's remarks above, the breach ultimately came down to poor cloud security, with data apparently exposed due to being shifted from a privately-controlled data store into the cloud.