Security News
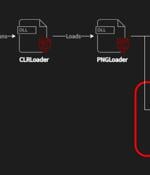
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.

A Hacker's Mind: How the Powerful Bend Society's Rules, and How to Bend them Back isn't about hacking computer systems; it's about hacking more general economic, political, and social systems. Once you start thinking of hacking in this way, you'll start seeing hacks everywhere.
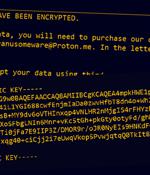
Microsoft on Thursday attributed the recent spate of ransomware incidents targeting transportation and logistics sectors in Ukraine and Poland to a threat cluster that shares overlaps with the Russian state-sponsored Sandworm group. The Microsoft Threat Intelligence Center is now tracking the threat actor under its element-themed moniker Iridium, citing overlaps with Sandworm.

The Australian Federal Police has pointed to Russia as the location of the attackers who breached local health insurer Medibank, accessed almost ten million customer records, and in recent days dumped some customer data onto the dark web. The release of customer data - some it containing intimate details of health services customers accessed using their insurance - came after Medibank refused to pay a ransom to secure the data on grounds that doing so would not guarantee customers' safety.

A series of attacks targeting transportation and logistics organizations in Ukraine and Poland with Prestige ransomware since October have been linked to an elite Russian military cyberespionage group. Researchers with Microsoft Security Threat Intelligence pinned the ransomware attacks on the Russian Sandworm threat group based on forensic artifacts and victimology, tradecraft, capabilities, and infrastructure overlapping with the group's previous activity.

A threat group tracked as 'Worok' hides malware within PNG images to infect victims' machines with information-stealing malware without raising alarms. Avast's report is based on additional artifacts the company captured from Worok attacks, confirming ESET's assumptions about the nature of the PNG files and adding new information on the type of malware payloads and the data exfiltration method.
Google has resolved a high-severity security issue affecting all Pixel smartphones that could be trivially exploited to unlock the devices. "The issue allowed an attacker with physical access to bypass the lock screen protections and gain complete access to the user's device," Schütz, who was awarded $70,000 for the lock screen bypass, said in a write-up of the flaw.

Given that the Silk Road website was very widely used for selling prohibited items, mostly recreational drugs but also stolen identities and other enablers of cybercrime, the adjective dark in the phrase "Dark web" came to be interpreted as dark-as-in-devilish-and-dangerous. Cybersecurity problems at Silk Road weren't limited just to Ulbricht's poor operational security.

The U.S. Department of Justice has announced today the conviction of James Zhong, a mysterious hacker who stole 50,000 bitcoins from the 'Silk Road' dark net marketplace. Zhong pled guilty to money laundering crimes on Friday, November 4, for exploiting a "Withdrawal processing flaw" that allowed him to withdraw many times more Bitcoin than he deposited on the dark web marketplace.

Microsoft is warning of an uptick in the nation-state and criminal actors increasingly leveraging publicly-disclosed zero-day vulnerabilities for breaching target environments. The tech giant, in its 114-page Digital Defense Report, said it has "Observed a reduction in the time between the announcement of a vulnerability and the commoditization of that vulnerability," making it imperative that organizations patch such exploits in a timely manner.