Security News

The author, a fluid writer and tech communicator, reveals how the tax code lends itself to hacking, as when tech companies like Apple and Google avoid paying billions of dollars by transferring profits out of the U.S. to corporate-friendly nations such as Ireland, then offshoring the "Disappeared" dollars to Bermuda, the Caymans, and other havens. Schneier cites "The Pudding Guy," who hacked an airline miles program by buying low-cost pudding cups in a promotion that, for $3,150, netted him 1.2 million miles and "Lifetime Gold frequent flier status." Since it was all within the letter if not the spirit of the offer, "The company paid up." The companies often do, because they're gaming systems themselves.

State-backed Chinese hackers launched a spearphishing campaign to deliver custom malware stored in Google Drive to government, research, and academic organizations worldwide. The Chinese hackers used Google accounts to send their targets email messages with lures that tricked them into downloading custom malware from Google Drive links.
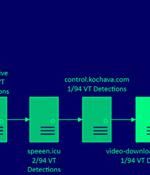
Users clicking on a link sent through the messaging app are directed to an actor-controlled site, which, in turn, sends them to a landing domain impersonating a well-known brand, from where the victims are once again taken to sites distributing fraudulent apps and bogus rewards. Attacks wherein scammy mobile ads are clicked from an Android device have been observed to culminate in the deployment of a mobile trojan called Triada, which was recently spotted propagating via fake WhatsApp apps.

Iranian government-sponsored threat actors have been blamed for compromising a U.S. federal agency by taking advantage of the Log4Shell vulnerability in an unpatched VMware Horizon server. "Cyber threat actors exploited the Log4Shell vulnerability in an unpatched VMware Horizon server, installed XMRig crypto mining software, moved laterally to the domain controller, compromised credentials, and then implanted Ngrok reverse proxies on several hosts to maintain persistence," CISA noted.
Hackers tied to the North Korean government have been observed using an updated version of a backdoor known as Dtrack targeting a wide range of industries in Germany, Brazil, India, Italy, Mexico, Switzerland, Saudi Arabia, Turkey and the U.S. "Dtrack allows criminals to upload, download, start or delete files on the victim host," Kaspersky researchers Konstantin Zykov and Jornt van der Wiel said in a report. Discovered in September 2019, the malware has been previously deployed in a cyber attack aimed at a nuclear power plant in India, with more recent intrusions using Dtrack as part of Maui ransomware attacks.

The attackers compromised the federal network after hacking into an unpatched VMware Horizon server using an exploit targeting the Log4Shell remote code execution vulnerability. After deploying the cryptocurrency miner, the Iranian threat actors also set up reverse proxies on compromised servers to maintain persistence within the FCEB agency's network.

North Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and Latin America. In the new campaign, Kaspersky has seen DTrack distributed using filenames commonly associated with legitimate executables.

A suspected Chinese state-sponsored actor breached a digital certificate authority as well as government and defense agencies located in different countries in Asia as part of an ongoing campaign since at least March 2022. Symantec, by Broadcom Software, linked the attacks to an adversarial group it tracks under the name Billbug, citing the use of tools previously attributed to this actor.

A cyberespionage threat actor tracked as Billbug has been running a campaign targeting a certificate authority, government agencies, and defense organizations in several countries in Asia. Symantec hasn't determined how Billbug gains initial access to the target networks but they have seen evidence of this happening by exploiting public-facing apps with known vulnerabilities.

The Russian scooter-sharing service Whoosh has confirmed a data breach after hackers started to sell a database containing the details of 7.2 million customers on a hacking forum. On Friday, a threat actor began selling the stolen data on a hacking forum, which allegedly contains promotion codes that can be used to access the service for free, as well as partial user identification and payment card data.