Security News

In the private sector, health insurance firm Accuro reported an illegal download and dissemination of corporate data following the Mercury IT attack. Even while new forms of authentication are being developed to make passwords obsolete, passwords remain the most common and most vulnerable method of securing data.

A Russia-linked threat actor has been observed deploying a new information-stealing malware in cyber attacks targeting Ukraine. Dubbed Graphiron by Broadcom-owned Symantec, the malware is the handiwork of an espionage group known as Nodaria, which is tracked by the Computer Emergency Response Team of Ukraine as UAC-0056.

During a webinar called The Hacker Mindset, a Red Team Researcher shared how you can use some of these tools for your own detection and prevention of breaches. The hacker mindset can be characterized by three core values: a strong sense of curiosity, an adversarial attitude, and persistence.

The Russian hacking group known as 'Nodaria' is using a new information-stealing malware called 'Graphiron' to steal data from Ukrainian organizations. Symantec's threat research team discovered that Nodaria has been using Graphiron in attacks since at least October 2022 through mid-January 2023.

A Russian national on February 7, 2023, pleaded guilty in the U.S. to money laundering charges and for attempting to conceal the source of funds obtained in connection with Ryuk ransomware attacks. "Between at least August 2018 and August 2021, Dubnikov and his co-conspirators laundered the proceeds of Ryuk ransomware attacks on individuals and organizations throughout the United States and abroad," the Department of Justice said.
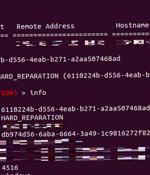
Threat actors are leveraging known flaws in Sunlogin software to deploy the Sliver command-and-control framework for carrying out post-exploitation activities. The findings come from AhnLab Security Emergency response Center, which found that security vulnerabilities in Sunlogin, a remote desktop program developed in China, are being abused to deploy a wide range of payloads.

A new hacking campaign exploits Sunlogin flaws to deploy the Sliver post-exploitation toolkit and launch Windows Bring Your Own Vulnerable Driver attacks to disable security software. According to a report by the AhnLab Security Emergency Response Center, recently observed attacks target two 2022 vulnerabilities in Sunlogin, a remote-control software by a Chinese developer.

A zero-day vulnerability affecting Fortra's GoAnywhere MFT managed file transfer application is being actively exploited in the wild. The vulnerability is a case of remote code injection that requires access to the administrative console of the application, making it imperative that the systems are not exposed to the public internet.

I have done a written interview and a podcast interview about the book. It's been chosen as a "February 2023 Must-Read Book" by the Next Big Idea Club.

The developers of the GoAnywhere MFT file transfer solution are warning customers of zero-day remote code execution vulnerability on exposed administrator consoles. GoAnywhere is a secure web file transfer solution that allows companies to securely transfer encrypted files with their partners while keeping detailed audit logs of who accessed the files.