Security News

GitLab has fixed a critical vulnerability in the Enterprise Edition and Community Edition of its widely used DevOps platform. "Scan execution policy allows configuring built-in scanners for GitLab projects, such as static analysis and vulnerability scanning. These scanners are running in dedicated pipelines with a predefined set of permissions," Alex Ilgayev, head of security research at Cycode told Help Net Security.

GitLab has shipped security patches to resolve a critical flaw that allows an attacker to run pipelines as another user. The issue, tracked as CVE-2023-5009 (CVSS score: 9.6), impacts all versions...

GitLab has released security updates to address a critical severity vulnerability that allows attackers to run pipelines as other users via scheduled security scan policies. The flaw was assigned CVE-2023-4998 and impacts GitLab Community Edition and Enterprise Edition versions 13.12 through 16.2.7 and versions 16.3 through 16.3.4.
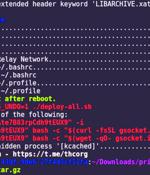
A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw in GitLab as part of a cryptojacking and proxyjacking campaign. Proxyjacking allows the attacker to rent the compromised host out to a proxy network, making it possible to monetize the unused bandwidth.

GitLab announced on Monday the new GitLab 16 platform, an upgraded and comprehensive AI-driven DevSecOps solution. GitLab 16 includes more than 55 improvements and new features.

GitLab has released an emergency security update, version 16.0.1, to address a maximum severity path traversal flaw tracked as CVE-2023-2825.GitLab is a web-based Git repository for developer teams that need to manage their code remotely and has approximately 30 million registered users and one million paying customers.

Phishing PyPI users: Attackers compromise legitimate projects to push malwarePyPI, the official third-party software repository for Python packages, is warning about a phishing campaign targeting its users. DDoS tales from the SOCIn this Help Net Security video, Bryant Rump, Principal Security Architect at Neustar Security Services, talks about the challenges of mitigating immense DDoS attacks.

GitLab is urging users to install a security update for branches 15.1, 15.2, and 15.3 of its community and enterprise editions to fix a critical vulnerability that could enable an attacker to perform remote command execution via Github import.The latest GitLab versions that address the problem are 15.3.1, 15.2.3, and 15.1.5, which users are advised to upgrade to immediately.

GitLab has fixed a remote code execution vulnerability affecting the Community and the Enterprise Edition of its DevOps platform, and has urged admins to upgrade their GitLab instances immediately. CVE-2022-2884 is a critical severity issue that may allow an authenticated user to achieve remote code execution via the Import from GitHub API endpoint, the company explained.

DevOps platform GitLab this week issued patches to address a critical security flaw in its software that could lead to arbitrary code execution on affected systems. Tracked as CVE-2022-2884, the issue is rated 9.9 on the CVSS vulnerability scoring system and impacts all versions of GitLab Community Edition and Enterprise Edition starting from 11.3.4 before 15.1.5, 15.2 before 15.2.3, and 15.3 before 15.3.1.