Security News

A new Mirai-based malware campaign is actively exploiting unpatched vulnerabilities in Internet of Things (IoT) devices, including DigiEver DS-2105 Pro DVRs. [...]

Adobe has released out-of-band security updates to address a critical ColdFusion vulnerability with proof-of-concept exploit code. [...]

Fortinet has issued an advisory for a now-patched critical security flaw impacting Wireless LAN Manager (FortiWLM) that could lead to disclosure of sensitive information. The vulnerability,...

You applied the patch that could stop possible RCE attacks last week, right? A critical security hole in Apache Struts 2, patched last week, is now being exploited using publicly available...

A new social engineering campaign has leveraged Microsoft Teams as a way to facilitate the deployment of a known malware called DarkGate. "An attacker used social engineering via a Microsoft Teams...
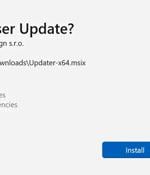
Bogus software update lures are being used by threat actors to deliver a new stealer malware called CoinLurker. "Written in Go, CoinLurker employs cutting-edge obfuscation and anti-analysis...

Cybersecurity researchers have discovered a new PHP-based backdoor called Glutton that has been put to use in cyber attacks targeting China, the United States, Cambodia, Pakistan, and South...

A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000...

Details have emerged about a now-patched security vulnerability in Apple's iOS and macOS that, if successfully exploited, could sidestep the Transparency, Consent, and Control (TCC) framework and...
A newly devised technique leverages a Windows accessibility framework called UI Automation (UIA) to perform a wide range of malicious activities without tipping off endpoint detection and response...