Security News

Hackers are actively exploiting a critical remote code execution flaw impacting the Brick Builder Theme to run malicious PHP code on vulnerable sites. The Bricks Builder Theme is a premium WordPress theme described as an innovative, community-driven visual site builder.

Microsoft says remote unauthenticated attackers can trivially exploit a critical Outlook security vulnerability that also lets them bypass the Office Protected View.Unauthenticated attackers can exploit CVE-2024-21413 remotely in low-complexity attacks that don't require user interaction.

Hackers are exploiting a server-side request forgery vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy the new DSLog backdoor on vulnerable devices. The flaw impacts the SAML component of the mentioned products and allows attackers to bypass authentication and access restricted resources on Ivanti gateways running versions 9.x and 22.x. The updates that fix the problem are Ivanti Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Ivanti Policy Secure version 22.5R1.1, and ZTA version 22.6R1.3.

South Korean researchers have publicly disclosed an encryption flaw in the Rhysida ransomware encryptor, allowing the creation of a Windows decryptor to recover files for free. Victims of the Rhysida ransomware may use the tool to try to decrypt their files for free, but BleepingComputer cannot guarantee the tool's safety or effectiveness.

SiCat is an open-source tool for exploit research designed to source and compile information about exploits from open channels and internal databases. Performing exploit searches based on desired inputs and sources such as Exploit-DB, Exploit Alert, Packetstorm Security, NVD Database, and Metasploit modules.

Recent versions of the Raspberry Robin malware are stealthier and implement one-day exploits that are deployed only on systems that are susceptible to them. According to a report from Check Point, Raspberry Robin has recently used at least two exploits for 1-day flaws, which indicates that the malware operator either has the capability to develop the code or has sources that provide it.

The operators of Raspberry Robin are now using two new one-day exploits to achieve local privilege escalation, even as the malware continues to be refined and improved to make it stealthier than...

Researchers suspect the criminals behind the Raspberry Robin malware are now buying exploits for speedier cyberattacks. An exploit developer is thought by infosec pros to be either on the Raspberry Robin payroll or a close contact that sells them to the group - most likely the latter.
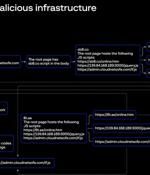
Employment agencies and retail companies chiefly located in the Asia-Pacific (APAC) region have been targeted by a previously undocumented threat actor known as ResumeLooters since early 2023 with...

Ivanti first disclosed the newest bug in the SAML component of of Ivanti Connect Secure and Ivanti Policy Secure appliances on January 31. "At the time of publication, the exploitation of CVE-2024-21893 appears to be targeted. Ivanti expects the threat actor to change their behavior and we expect a sharp increase in exploitation once this information is public - similar to what we observed on 11 January following the 10 January disclosure," Ivanti warned last week.