Security News

An advanced persistent threat group, dubbed ToddyCat, is believed behind a series of attacks targeting Microsoft Exchange servers of high-profile government and military installations in Asia and Europe. "The first wave of attacks exclusively targeted Microsoft Exchange Servers, which were compromised with Samurai, a sophisticated passive backdoor that usually works on ports 80 and 443," wrote Giampaolo Dedola security researcher at Kaspersky, in a report outlining the APT. Researchers said ToddyCat a is relatively new APT and there is "Little information about this actor."

An ongoing outage affects multiple Microsoft 365 services, with customers worldwide reporting delays, sign-in failures, and issues accessing their accounts. The affected services include the Exchange Online hosted email platform for businesses and the Microsoft Teams communication platform, as well as SharePoint Online, the Graph API, and Universal Print.

An advanced persistent threat group dubbed ToddyCat has been targeting Microsoft Exchange servers throughout Asia and Europe for more than a year, since at least December 2020. At the time, the hacking group exploited the ProxyLogon Exchange flaws that allowed them to gain remote code execution on vulnerable servers to deploy China Chopper web shells.

An advanced persistent threat group dubbed ToddyCat has been targeting Microsoft Exchange servers throughout Asia and Europe for more than a year, since at least December 2020. At the time, the hacking group exploited the ProxyLogon Exchange flaws that allowed them to gain remote code execution on vulnerable servers to deploy China Chopper web shells.

Microsoft is warning that the BlackCat ransomware crew is leveraging exploits for unpatched Exchange server vulnerabilities to gain access to targeted networks. Upon gaining an entry point, the attackers swiftly moved to gather information about the compromised machines, followed by carrying out credential theft and lateral movement activities, before harvesting intellectual property and dropping the ransomware payload. The entire sequence of events played out over the course of two full weeks, the Microsoft 365 Defender Threat Intelligence Team said in a report published this week.

Two of the more prolific cybercriminal groups, which in the past have deployed such high-profile ransomware families as Conti, Ryuk, REvil and Hive, have started adopting the BlackCat ransomware-as-as-service offering. The use of the modern Rust programming language to stabilize and port the code, the variable nature of RaaS, and growing adoption by affiliate groups all increase the chances that organizations will run into BlackCat - and have difficulty detecting it - according to researchers with the Microsoft 365 Defender Threat Intelligence Team.

Microsoft says BlackCat ransomware affiliates are now attacking Microsoft Exchange servers using exploits targeting unpatched vulnerabilities. Two weeks after the initial compromise using an unpatched Exchange server as an entry vector, the threat actor deployed BlackCat ransomware payloads across the network via PsExec.

What is cryptocurrency, and what is a crypto exchange? A crypto exchange is a digital transaction mechanism - essentially an online market - which allows you to buy and sell cryptocurrency.
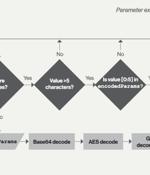
NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration. "Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.

Security researchers have found a new post-exploitation framework that they dubbed IceApple, deployed mainly on Microsoft Exchange servers across a wide geography. The researchers observed IceApple being deployed after the threat actor obtains initial access to the network belonging to organizations in various activity sectors: technology, academic, and government.